
Part three in the article series: Chips, formats, and encryption
Modern identity cards and credentials rely on encryption for security. It is what separates a smart card, high-frequency contactless card, or mobile credential from older insecure technology such as low-frequency proximity cards, magstripes, and barcodes.
But what is encryption and how does it work in the credential world?
At the heart of this question is the encryption key, a string of data used to encode and decode information. In most card systems, there is a secret key that is shared between the card and reader enabling secure transactions to occur within the system.
Each concept is applicable to both cards and mobile credentials, and understanding them is key to making informed decisions for your campus card program.
“You can think of it as the variable in an equation – the equation stays the same, but the variable can change,” says David Stallsmith, ColorID’s Director of Product Management. “The credential and the readers must know the correct secret key to encrypt and decrypt the identity data.”
Only then will they communicate to open doors or conduct transactions. That's why encryption is the key to security.
Traditionally, most manufacturers have used their own standard encryption key in all their clients’ readers and cards.
Of late, however, there has been a push by some end users – including some campuses – for custom keys. Rather than using the manufacturer’s standard keys, these clients have requested dedicated keys unique to their system.
There are benefits and drawbacks to both approaches.
Standard or non-custom keys make ordering and provisioning of new cards and readers easier, faster, and sometimes cheaper. That is because the manufacturer does not need to customize them for the individual client.
But that positive also comes with a negative. Using the manufacturer’s standard key ties you to that manufacturer for cards and readers. The ability to order from multiple suppliers is reduced or even eliminated.
People that owned their custom keys during the pandemic had more options for card stock suppliers, but since the supply chain bounced back, that benefit has pretty much evaporated.
Another drawback of non-custom keys is that if the manufacturer’s standard key is compromised, it could impact all client sites. This could require replacement or reprogramming of all cards and readers.
Protection against a compromise at the manufacturer level is a benefit of custom keys. If it were to happen, end users with custom keys would not be impacted. It is important to remember, however, that custom keys are not immune to compromise. If not properly protected, they are arguably as vulnerable as non-custom keys.
“Depending on what type of card it is and how you manage that custom key, it can give you the ability to do other things,” says Todd Brooks, Vice President of Products and Technology at ColorID. “It can provide a bit of freedom as far as how you get your cards and how you encode the cards.”
For example, with custom keys the end user can program cards on their own rather than relying on the manufacturer do it. This allows them to buy cards from multiple suppliers.
“People that owned their custom keys during the pandemic had more options for card stock suppliers,” says Stallsmith. “This cut months off their lead time for card orders, but since the supply chain bounced back, that benefit has pretty much evaporated.”
Determining whether you want custom or non-custom keys is just the first decision. Next you need to decide if you’ll have your manufacturer hold those keys on your behalf or if you want to hold your keys within the institution.
At face value, holding your own keys – what some industry vendors call ‘owning your keys’ – seems like the obvious choice. Again, however, complexities arise.
Managing the keys yourself can be expensive and if not done properly can leave you vulnerable.
Most campuses wanting the benefits of custom keys have determined that they are not ready for the responsibility and liability of managing those keys on their own.
“When the manufacturer is holding the custom keys for you, there's security in that,” explains Brooks. “Managing the keys yourself can be very expensive and if not done properly can leave you vulnerable.”
Though far from the norm, he says, a small number of campuses have opted to manage their own keys, control their entire ecosystem, and decide how they're going to make their cards work on the different reader models they wish to use. It takes a more effort and more IT expertise, but it can be done.
Whether an institution uses custom keys or not, data needs to be encoded on the cards.
“Generally, cards are pre-programmed by a manufacturer like an HID or Allegion even if the end user has a custom key,” says Brooks. “In some cases, however, the campus will do it themselves either in the card printer using ID software or with a desktop device or USB reader.”
The idea of holding your own keys so you have total control of your system is attractive, but the practical application is limited.
To accomplish this, a Secure Access Module (SAM) that is purpose-built to securely stores keys is used.
“Whether it's a USB device or it's in the printer, it's basically the same SAM module,” says Brooks.
Very few campuses have taken on the responsibility to own or hold their own custom keys, so it is difficult to measure the value of doing so. Conceptually there are benefits, but they may just be conceptual at this point.
“The idea of holding your own keys so you have total control of your system is attractive, but the practical application is limited,” says Stallsmith.
He uses the example of a campus holding the custom keys for their DESfire cards. If the institution decides to change their access control reader manufacturer, it is true that holding keys could streamline the process. But there are only a few reader manufacturers to choose from, and ripping and replacing one access control reader for another is not an attractive or common decision.
“Sure, you can hold your own keys, but it's not like all of a sudden your world is going to dramatically change,” he says. “But if you have a very specific use, then then I guess it could be helpful.”
 Encryption keys and transaction system providers
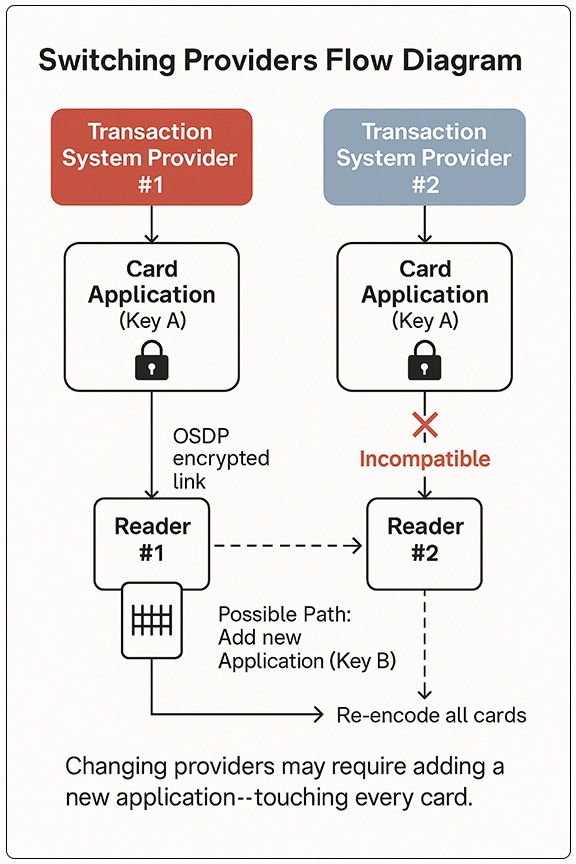
Encryption keys and transaction system providersIt is a common question: If I have custom keys or if I hold my own custom keys, does it make it easy to switch from one transaction system provider to another? The real question is more nuanced. You are really asking: Could I switch providers but continue to use my existing cards and readers?
In theory, you could because DESFire and other modern contactless credentials can store multiple applications on the same card. In most cases, however, the prior application will not work in the other transaction system provider’s readers and system.
“Just because you own your key doesn't mean that application you create using it will work on the different readers,” says Brooks. “It may require you to put two, three, or four different applications on the card itself to work with the reader infrastructure from the different transaction system providers.”
Think of it this way. You have an application on your card that is used in transaction system vendor #1’s platform. You replace vendor #1 for vendor #2. Just because you hold the encryption key and that key was used to create the first application does not mean it will work in vendor #2’s platform. The data, the format, and other elements would likely make them incompatible.
Of course, with modern multi-application cards, you could reprogram the cards to add a new application that supports vendor #2’s system, but that is easier said than done. It would require you to touch every existing card to add the new application. In a campus environment with thousands or tens of thousands of individual users, it just is not a realistic ask.
Stallsmith states it this way: “In a university setting, you don't get cards back.”
Though it garners a lot of discussion, it is rare for higher ed institutions to own or hold their own encryption keys. It can be costly, and it requires solid IT capability and commitment.
“I would say the key ownership discussion so far is largely theoretical,” says Stallsmith. “We've helped a number of customers get custom keys from manufacturers, which is often not easy because they haven't had to do it much.”
With OSDP you can centrally roll keys and not have to go from reader to reader to make changes. That makes the conversation around custom keys a lot more interesting.
This may change as access control readers move from using the older Wiegand protocol to the new OSDP protocol in greater numbers.
With the Wiegand protocol, the access control system can receive data like card numbers from the reader, but it cannot send information to the reader. The OSDP protocol, on the other hand, facilitates two-way communication between readers and the access control system. This enables the system to send new encryption keys to readers remotely without requiring a human to visit each reader for manual updates.
“With OSDP you can centrally roll keys and not have to go from reader to reader to make changes,” says Stallsmith. “At that point the conversation around custom keys is going to get a lot more interesting."
For most campuses, that's years away. For those with the means to do it now, however, there are more options.
The large card and reader manufacturers have been creating credentials with secure encryption keys for decades now.
While security breach and system compromise should always be top of mind, neither Stallsmith nor Brooks could point to a single instance of card or credential compromise at a systemwide encryption key level. This is true for both manufacturer’s standard keys and end user custom keys.
So, while real, to this point the threat is likely overblown.
Traditional large manufacturers are incredibly consistent at programming and delivering readers and cards. Another manufacturer may give you a custom key, but they may have a devil of time making cards on time.
This leads Stallsmith to point out that there's another side to the custom key discussion. He says that the traditional large manufacturers are incredibly consistent in their ability to program, update, and deliver readers and cards that work together.
“You just buy their readers, and you buy their cards, and everything works,” he says. “You can go with another manufacturer, they'll give you a custom key, but they may have a devil of time making cards on time.”
Perhaps the lesson is that it's not just the concept of the custom key that should determine what readers and cards a campus elects to use.
Like most decisions, there are many factors at play. In this series of articles, we addressed three of the most important – chips, formats, and encryption. Evaluating each of these concepts can help you make the best decisions for your campus.




