
Part two in the article series: Chips, formats, and encryption
In the second article in our series titled Chips, formats, and encryption – we explore card formats. In the previous article, we learned that chips store and process data, but it is the format that defines the specifics of the data – the number of digits in the string and what each area of the string means.
Consider this series of digits, 2024567041. Now look at it this way, (202) 456-7041. An established format defines that a phone number will include ten digits with the first three standardized as the area code.
The format provides order, but the format is not the actual number. That unique number identifies – or dials – the White House.
Similarly, a format defines the way data is stored on the credential, but each cardholder has a unique number.
You often hear an end user say ‘I have a 35-bit card,’ but they are confusing the 35-bit format with the card or chip itself.
For identity and access control professionals, the differences between chips, cards, formats, and numbers are subtle. They are, however, crucial to managing systems.
Understanding the options within each category can ensure you make the most appropriate selections for your campus. It is also crucial in ongoing purchasing processes to make sure you are specifying cards, formats, and numbers that will work in your environment.
Each concept is applicable to both cards and mobile credentials, and understanding them is key to making informed decisions for your campus card program.
“It is always a challenge to explain to customers the difference,” says Todd Brooks, Vice President of Products and Technology at ColorID. “You hear ‘I have a 35-bit card,’ but they are confusing the 35-bit format with the card or chip itself.”
He explains that the same format can be used on any card type, because the format is just the way the data is parsed.
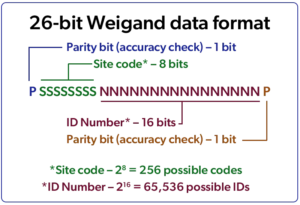
The 26-bit format – also known as the Weigand format – is the oldest and most common. It allows for the smallest number of digits, however, and this provides limitations.
A bit is a binary term for a zero or a one. Thus, 26-bit format consists of 26 zeros or ones laid out in a specific pattern. The initial bits form the three-digit site code with 256 total options. The remaining bits form the ID number with 65,536 options.
The initial bits form the three-digit site code with 256 total options. With that limited number of unique codes for organizations worldwide, there are plenty of duplicates.
The limitation is that with only 256 site codes for organizations around the world, there are plenty of duplicates. While 65,536 seems like a lot of unique numbers, many organizations have thousands of cardholders.
Any card reseller worldwide can issue 26-bit cards so there is no control over numbering systems.
“Because 26-bit is an open protocol, no entity is managing the number range so if care is not taken when placing orders, programmed ID numbers can overlap from one order to the next,” says David Stallsmith, ColorID’s Director of Product Management. “If this occurs, the new batch of cards cannot be entered into your system because the numbers are already in use.”
 Moving beyond 26-bit
Moving beyond 26-bitDespite the industry’s concerns, the 26-bit ‘OG’ format remains difficult to displace.
“It works in everybody's system, and some older access control systems can only handle 26-bit,” says Stallsmith. “Even when systems support longer formats, many security managers are reluctant to use them.”
But he stresses that upgrading to more versatile formats makes sense. That is why security-conscious organizations have moved beyond 26-bit.
We highly recommend against starting with a 26-bit format. HID and Allegion offer formats of 35-bit, 40-bit, 48-bit, and they will manage the number range for you.
“We highly recommend against starting with a 26-bit format,” Stallsmith says. “HID and Allegion offer formats of 35-bit, 40-bit, 48-bit, and they will manage the number range for each customer which is a nice feature.”
The longer the bit structure, the more digits can be stored. The more digits, the more uniqueness for site codes and credential numbers. This is crucial to the successful operation of all the systems that use cards to authenticate and grant access, but it is not the same as data security.
“True security is in the chip and encryption, not in the format,” says ColorID’s Brooks.
There are thousands of other formats, but many are custom and can only be purchased from specific dealers. In some cases, manufacturers will create one for a specific dealer, and they will only supply cards with the format to that dealer.
Dealers often claim that it provides an added layer of security, allowing them to further tighten the grip against card number duplication.
Stallsmith says that this added layer does little to nothing for security, and it forces the end customer to buy all cards through the dealer.
“The real security here is protecting the dealer's business,” jokes Stallsmith. “Make sure you're buying a format that's generally available from all dealers who sell that product.”
Since most campus cards are used in access control systems, they typically use one of the formats described above. In addition to the unique ID number required for the security system, however, the same card will often need to contain one or more additional unique IDs.
A common ID number that is used by the institution’s campus card system provider is a 16-digit ISO number. Additionally, dedicated user IDs for applications like library checkout are sometimes used.
If you are planning to move to mobile, find out from your intended provider what formats they support and consider migrating your card population to that format.
“In some cases, the access and campus card systems themselves are modified to support a single ID that is stored on the card using a single format,” explains Brooks. “But in other cases, the card contains multiple numbers, each designed to support specific functions.”
Modern, multi-application contactless cards are built to support this exact situation. Multiple numbers can be stored in the same contactless card, and each can use a different format.
Though it is not always the case, most modern access control systems can support multiple formats.
But, as Stallsmith explains, end users typically prefer all their credential types to be programmed with the same format.
“If you are planning to move to mobile, find out from your intended provider what formats they support for issuing mobile credentials,” he says. “And consider migrating your card population to that format.”




