
“It’s no longer simply about putting a photo on a white piece of plastic,” says Ryan Park, Fargo Electronics’ director of product marketing for secure printers/encoders. “It’s just not secure. Unfortunately, that represents a lot of the ID vehicles out there today. There are very few applications in the ID card world that don’t have a need for security.”
The need for greater security in the issuance process is what’s driving Fargo today. “Two years ago, we (Fargo) decided to step off the path, to not be a printer company anymore but a secure card program producer. We’re looking at all the places, cradle to grave, that could be vulnerable. Our message as a company is that we’ve expanded from printers to helping our customers issue secure credentials. In a post 9-11 world, we’ve seen a rapid increase in ID theft. Previously, we’ve focused on our printers, simply putting photos on cards. We now also want to be the best at securing the entire process.”
He said there are three elements to security: “The printer you choose, securing the card itself and having the process and personnel in place for when it comes out of the machine.”
Printer
As to the printers themselves, many have their own security features, he said, such “as the ability to load cards into the machine, then lock the access doors, or the ability to lock up the materials section of the printers so operators can’t access them.”
Some Fargo customers have gone so far as to bolt the printer to something immoveable, like a vault. “One of the things we’ve learned is you can have all the alarm bells in the world, but if someone is willing to crash a truck through a wall, you want to bolt the printer to something that can’t be moved,” said Mr. Park.
He calls it “lock and bolt. It’s your best defense.”
Another solution: “Give your printer some business rules,” he said. “For example you could define at what hours should the cards be produced. We know that cards being produced on the weekend may still may be legitimate, but it’s something we need to know about. Or you can determine which operators can physically use the product. The printer can periodically ask for code words that only certain parties should know.”
He said there are a “handful of features where a printer can be self-aware. You can set it up so every time a job is produced, a password is needed. Or you can use biometrics, where the operator might have to give his thumbprint. But at same time, you might have this bad person in the office and you want to prevent him from grabbing the materials so he can produce an ID outside the office. That’s where something like a secure vault comes in handy. You make sure the cards are locked up in the printer. Outside the printer you need to do inventory counts.”
Securing the Card
“The first thing you have to identify is what are the truly sensitive pieces of the process,” he said. “Are you a university utilizing a tamper-proof hologram? While anyone can buy a card printer, a hologram is something you can control.”
The purpose here – whether at a university, a major corporation, or as a federal agency or one that is supplying the feds – is to make the card counterfeit-resistant.
“At the very highest level, such as with a government agency, you want to control the movement of your hologram at all stages,” said Mr. Park. “For example, a hologram could be shipped by armored car, controlling the entire process. These are services we offer for very sensitive applications.” He said the street figure for these kinds of holograms would reach six figures, which is why securing them is so important.
Process and Personnel
“You’ve got this fantastic card you’re producing with smart encrypted chips and holograms, but you’re using temp labor to produce the cards, and all of a sudden 1,000 cards end up on the black market,” said Mr. Park. “You actually have to secure the production of that card.”
With cards that are instantly produced, “you’re basically postponing production of the card as long as feasible so the card is produced and given to the customer as soon as possible. It’s encoded in the machine and it goes directly to you. Once it’s produced, it’s now a valid entity. The more you can shrink that time the more secure it is.” Driver licenses are a good example. Some states utilize a central issuance facility, while most instantly produce the licenses and distribute them right away to applicants, he added.
“We’re talking about back-end production, but it’s very critical at the front end, too,” he said. “A driver license can be produced in a valid way but you could still end up with a forged driver license.”
The chain and its weakest link
As the old saying goes, a chain is only as strong as its weakest link. When it comes to issuance of secure identity credentials, the chain involves the securing the printer, the card, and the process. To improve your issuance security, make sure all three are evaluated on a regular basis.
 Colleges have other options for cell phone alerts, of course. They could go off campus and hire a company specializing in text messaging. That’s what Rave Wireless and Mobile Campus are offering to universities.
Colleges have other options for cell phone alerts, of course. They could go off campus and hire a company specializing in text messaging. That’s what Rave Wireless and Mobile Campus are offering to universities.
Rave offers what its COO, Raju Rishi, calls “an alert solution, which basically gives the university the ability to get emergency broadcasting to the entire school or a subset of the school (like students who live on campus), whether it’s about a gas leak or orientation. The university pays us for that capability yearly. We tie into Blackboard (campus card solution),” he added, “so we don’t have to recreate the lists.”
This alert solution costs a college about $10,000 a year. “It gives students unlimited text messaging plans,” added Mr. Rishi.
He said the plan works with all cell phone carriers, email, and web mail. So if the student doesn’t have a cell phone, he can still receive an email alert.
Rave also offers a full-blown cell phone solution called Rave Campus that is tied to a specific carrier. At Atlanta-based Mercer University, Rave Campus recently announced a tie-in with Sprint. “With this you get additional features like really reduced phone rates and other options,” said Mr. Rishi. And of course, the program includes the emergency text notification feature.
“Rave Alert is designed to work with any cell phone. Rave Campus is designed around a (specific) phone model (and carrier),” he added.
The company currently serves about 25 campuses, about half which use just Rave Alert and the other half Rave Campus. By the end of the year, Mr. Rishi said he expects to have 60 or 70 campuses in one or the other program.
While Rave’s alert feature is nice, said Michael Belote, Mercer’s vice president of information technology, that’s not the reason the Macon, Ga.-based school went with Rave. “Most students are into instant communication instead of email. They’re using MySpace, Facebook and text messaging. We’re just adapting our communications technologies to meet the needs of today’s students.”
In fact, the decision to go with Rave, and its enhanced text messaging features, came in March, about a month before the Virginia Tech shooting.
“There is certainly a safety component of Rave Wireless but we see a lot of value in some of the applications that Rave provides in building the community, enhancing student learning as well as the safety features,” added Mr. Belote.
The phones are free to students and the $32.50 base plan includes unlimited text messaging, free nights and weekend calls and unlimited calling using Mercer’s Mobile Network, explains Mr. Belote. Full deployment is expected to take place this August, in time for fall enrollment.
He said if a student decides to keep his existing phone, he can still sign up with the college to receive emergency or other types of text messaging alerts.
Mobile Campus uses advertising to support free alert messaging
Another option is Mobile Campus, Atlanta, GA. It offers free text messaging to university students in exchange for the students agreeing to receive advertisements a couple times a day.
Jim Ryan, president and CEO for Mobile Campus, said the company gives university administrators a web-based interface to communicate with students.
“The first thing you need is for students to opt in to receive the messages. Probably the most effective means to reach your students is via SMS,” said Mr. Ryan, former head of AT&T’s wireless data services division. “When Virginia Tech happened, people became more interested in SMS as a way to communicate with their student bodies and we got a lot of calls.”
In a perfect world, that would be all that’s needed. But cell phones aren’t perfect. “The challenge is we don’t own the SMS infrastructure,” said Mr. Ryan. “All we can do is place the message out there for delivery. But (carrier) capacity and various other challenges will determine how long it will take to get the message to the individual,” he said.
Text messages delivered around the country shouldn’t be a problem, “but when you’re delivering SMS in a given geography, when you try to send 30,000 messages through one cell site, that’s when you run into capacity (problems),” he added.
That’s why he believes universities should concentrate on delivering “something that’s multi-modal–text messaging and email–so if one fails, the other works,” he said.
While Mobile Campus’ text messaging service can reach “a significant portion of the student body,” says Mr. Ryan, “we don’t have to reach 100% of the students to get the message out. Even if you hit 40%, the rest will know pretty quickly simply by word of mouth.”
He said 14 universities have signed so far with Mobile Campus and “we’re actively seeking to serve another 11. We expect in the fall to have quite a large constituency signed up.”
Texas A&M selected CBORD’s Foodservice Suite® to power their dining services operation. The institution will also use the company’s NetNutrition® online nutritional analysis programand EventMaster® PLUS! catering and event management solution. Texas A&M has 47,000 students, 10,000 in residence halls, and 8200 on board plans.
Texas A&M University selects CBORD’s Foodservice Suite
University purchases software to improve margins and efficiency
Ithaca, New York: The CBORD Group, Inc. is pleased to announce that Texas A&M University in College Station, TX recently selected the company as its food service management technology provider. Texas A&M converted to the Foodservice Suite® modular software package on account of its flexible integration capabilities, user-friendly design, and superior client support.
Texas A&M uses Foodservice Suite to handle menu and recipe management and improve inventory control, reducing waste and increasing accuracy. The university also chose to implement CBORD’s NetNutrition® online nutritional analysis program, along with its EventMaster® PLUS! catering and event management solution. Both products are fully integrated with Foodservice Suite, allowing employees and customers alike to enjoy a seamless user experience with the most up-to-date information.
Foodservice Suite is a leader in the college and university marketplace for improving margins and increasing customer and employee satisfaction by automating campus food service operations. The scalable software package supports functionality for menu management, recipe scaling, nutritional analysis, inventory management, purchasing, and much more. Furthermore, the system’s tight integration with other CBORD® offerings, such as campus card systems, online ordering solutions, catering and event management software, and online nutritional analysis tools, makes it easy for universities to see the “big picture” of auxiliary operations.
The purchase of Foodservice Suite is one of many strategic changes Texas A&M’s food service operations have undergone for the purpose of improving student services under the leadership of Nadeem E. Siddiqui, Executive Director, Dining Services. In fact, the students at Texas A&M recently named Siddiqui Administrator of the Year in recognition of the dedication to student satisfaction he and his staff have displayed.
“We are excited to team up with The CBORD Group to advance and develop our dining program and to ensure the best dining program for our wonderful Aggie community,” says Siddiqui.
“Mr. Siddiqui’s team at Texas A&M has a long history of commitment to student services, and we are very pleased to assist them in refining their food service operations,” says Randy Eckels, Senior Vice President, Sales and Marketing, The CBORD Group, Inc. “Our user-friendly software automates back-end processes, allowing university employees to focus on the quality customer service Nadeem and his staff exhibit every day. We are glad to play a role in their success.”
Texas A&M University currently enrolls 47,000 students. It has a residence hall population of 10,000, with 8,200 students on board plans.
About The CBORD Group, Inc.
The CBORD Group serves colleges and universities, corporations, healthcare facilities, chain restaurants, supermarkets, and a host of other market segments. CBORD’s products are used in food service, catering, nutrition services, online ordering, meal plans, campus ID card privilege control, access control, integrated security, housing services, and other institution-wide activities. The CBORD Group serves more than 6,000 clients in the U.S., Canada, Europe, South Africa, the Middle East, New Zealand, and Australia.
The CBORD Group was founded in 1975. Today it employs more than 475 professionals. To learn more about CBORD, visit us at www.cbord.com.
By Jerry Banks and Les G. Thompson, co-authors of RFID Applied
Under ideal conditions, the popular Alien Squiggle RFID tag can be read at a distance of approximately 20 meters. But what happens if it is placed behind a glass of water? What about placing it to the side, but adjacent to the glass of water? How about placing it in the water?

Answers to these and other questions will appear later, but suffice it to say that the readability of a tag is affected by the placement of the tag and its ambient environment.
When we discuss passive RFID tags with an audience of people that have never seen a tag, or, if they have seen one, they didn't know what it was, we say first that reading the tags is impacted by the release of radio frequency waves in the ambient environment. We ask for examples in the room in which we are making the presentation. We ask you, the reader, to ponder this question before reading the next paragraph.
Here is a hint: Typically, we are making a presentation using PowerPoint. So, there is a computer and a projection device involved. Both of those emit radio frequencies. How about the cell phones in every attendee's possession? What about the lights and the dimmer switches? So, even in an innocuous place like an auditorium, there are ambient sources of radio frequency that interfere with the very weak signal that a passive RFID tag can generate.
So far, you have some speculation that moisture has an impact on the Alien Squiggle tag. And, you have been told that ambient sources of radio frequency waves impact RFID tags, particularly passive tags that don't have a power source.
We aren't selling the Alien Squiggle tag. But, why are there so many different RFID tag designs? For that, we turn to the subject of frequencies.
For convenience sake, the entire RF spectrum has been segregated into bands of frequencies that tend to share common characteristics. Table 1 describes these classifications. You should notice that as the frequency of the wave increases, the length of the wave decreases.
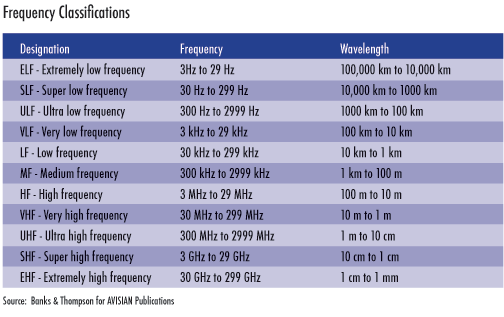
In the previous article, "The black art of RFID antennas," we discussed how to construct a tag based on a target communication frequency, but we did not discuss why a company like Texas Instruments or Alien Technologies would create a suite of tag products, each tag targeting a different frequency. The simple answer is that radio waves at different frequencies interact with their environment differently.
Imagine that you are standing in a large open. If you were to sing a variety of notes, you might eventually sing a note that seems to fill the room with sound much more than the other notes. The note that you found is produced by a sound wave that has the appropriate wavelength to resonate perfectly in the room. This is why most people think that they can sing better in the shower. If you were to change the environment, the note required to produce a resonating sound would change. For instance, if a wood table was placed in the room, the note that resonated in the room before may not still resonate like it once did, and another note may be found that resonates in the room better than the previous note. Sound waves are analogous to radio waves in this respect.
In the world of RFID, the wood table in the previous example may be analogous to another type of material such as paper, water, metal, or cloth that can change the environment. Upon further examination, the previous example is more complex than it seems. Why did the resonant frequency change when the table was placed in the room? The answer is that the table impeded the propagation of the sound wave. There are hundreds of factors that could influence why the wave was impeded, but the two most common are that 1) the sound wave was absorbed by the table, or 2) the sound wave was reflected by the table which disturbed the other waves that were bouncing around the room. Like waves on a pond, sound and radio waves can cancel each other if they collide.
The two most common environmental conditions on the minds of RFID practitioners are water and metals such as iron, lead, and aluminum. The pharmaceutical industry is worried about water because many drugs contain some type of moisture. The manufacturing industry is concerned with metal because assembly lines are usually made of metal and the products may also be made of or contain metal.
Why is water such a problem for RFID tags? The truth is that water is not a problem as long as the correct frequency is chosen. Microwave ovens are tuned to the resonant frequency of water so that they can absorb the energy from the radio waves and heat up our food. The oven produces radio waves at the 2.45 GHz frequency (microwaves). These waves have a wavelength of 12.24 cm. As the waves pass through the water in the food, the water molecules rotate to align themselves with the wave. The molecules rotate with each wavelength. This oscillation causes the increase in temperature. The structure of water molecules is perfect for interacting with this frequency. Other wavelengths would not cause the water molecules to rotate. For RFID, the absorption of energy has a negative consequence unless it is being primarily collected by the antenna attached to an RFID tag.
The microwave example illustrates why choosing a frequency in one of the higher bands such as UHF or SHF would not be a good choice for applications of RFID near water where HF bands work better. The tradeoff with employing a lower frequency is that there is a decrease in the data transmission speed between the reader and tag as the frequency decreases. HF RFID tags are most often used in close proximity to water. These types of tags have coil type antennas, which are designed to work best at lower frequencies. For more information about RFID antennas, please refer to Part 4 in this article series. Some RFID tag manufacturers, like IPico, have created dual-frequency tags to combat these issues. As the name implies, dual-frequency tags transmit at two different frequencies. These types of tags can achieve higher transmission rates when communication is possible at a higher frequency, yet the tag can always be read, even when placed in a glass of water because it can transmit at a lower frequency. These tags are more robust and more expensive.
Experimenting with RF tags and water
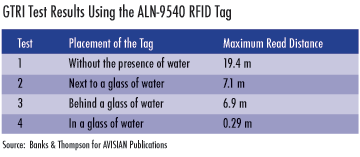
With this knowledge we can answer the questions posed at the beginning of this article. The Alien 9540 Squiggle tag adheres to the EPC Gen 2 standards and communicates at a frequency of 915 MHz. From what we have learned about the effects of water on radio waves in the UHF band, we can deduce that the signal and energy will be attenuated by the water. The electromagnetic field required by the tag will weaken as the tag is moved closer to the water until the tag will no longer operate unless the reader is extremely close to the tag. The exact effect cannot be determined with respect to the reduction in read range for a tag when measured outside of a controlled environment such as a laboratory. It is certain, however, that if a tag is placed in the water there will be a significant reduction in its read range. Now, what if a tag worked at the lower frequency of 13.56 MHz in the HF spectrum? We can predict that the tag will operate better than the UHF tag, but a tag that operates at 125 KHz could be read at a much further distance if it was submerged fully in the water.
At our request, the Electro-Optical Systems Laboratory at the Georgia Tech Research Institute (GTRI) conducted an experiment using the Alien 9540 Squiggle tag. As shown in Table 2, their tests demonstrated that the tag is affected by water as we would expect.
The effect on a radio wave is also influenced by some types of metal with which the wave is interacting. There are many elements on the periodic table that are classified as metals. Most of them are not used on a day-to-day basis. This discussion will pertain to the more common metals that an RFID tag may come in contact with such as iron, aluminum, and copper. Ferrous metals, such as iron are often regarded as having the worst effect on electromagnetic radiation because they are, for the most part, magnetic. Non-ferrous metals, like aluminum and copper, are not magnetic and interact better with electromagnetic radiation. Not all ferrous metals are magnetic and vice versa.
Metal (the kinds mentioned above this qualification won't be repeated every time we say the word "metal") can affect radio waves in several different ways. First, radio waves cannot penetrate these metals. If RF waves cannot penetrate a metal, the metal is said to be opaque to radio waves. It is interesting that these metals do not need to be solid to completely stop a radio wave. RF engineers work in sterile environments known as a Faraday cage. The Faraday cage has walls made of highly conductive metal mesh or screen that have holes smaller than the RF wavelength being tested. If the holes are small enough and the metal is thick enough, all radio waves will be absorbed and distributed along the surface of the screen.
Metal can detune a radio wave. Detuning occurs when the amplitude and/or wavelength of the wave is skewed if the wave comes in contact with the metal. Once the wave is detuned, it cannot couple with the RFID tag. In addition to detuning, the RFID waves form miniature RF eddies where they intersect the metal. These eddies effectively cancel out the wave such that it either dissipates completely or the wave is impeded to the point that it cannot couple with the tag.
Metal may also absorb some of the radio wave. This is known as parasitic capacitance. Just like water, the metal diminishes the strength of the radio wave by absorbing some of its energy. In active RFID systems, where energy is abundant, the metal can become a conduit for the RF energy. It is not uncommon for a gas or water pipe to channel a radio wave down a hall into another room or to another floor of the building. These types of occurrences can be very challenging for active tag real-time location systems because active tags transmit with so much more energy (wattage) than passive tags do. Any metal objects such as pipes or handrails can become a secondary antenna for the active tag's transmissions.
Understanding the characteristics of RF can aid in the successful planning and implementation of an RFID solution. The basic physical principles of RF are a necessary tool in the RFID practitioner's tool belt. It is important to remember that real world environments are much different than RF labs. Passive RFID systems are much more susceptible to harsh RF environments than active RFID systems. Even so, dynamic environments can cause even the most robust RFID systems to stumble unless they are designed correctly.

About this article:
We would like to thank Gisele Bennett and her group of researchers at the Electro-Optical Systems Laboratory at the Georgia Tech Research Institute for conducting the water readability tests referenced above.
This article is the fifth in an ongoing series that explains the principles of RFID. It was created for RFIDNews by Jerry Banks, Tecnológico de Monterrey, Monterrey, Mexico and Les G. Thompson, Lost Recovery Network, Inc., Atlanta, Georgia. The authors are two of four co-authors of RFID Applied, John Wiley, 2007, ISBN-10 0471793655; ISBN-13 978-041793656.
 Get a bunch of students, mostly freshmen, away from home for the first time. Stick them all in a dorm, many of them are armed with a checking account and checks, a credit card, a student ID card, their driver license and Social Security card. It’s a recipe for ID theft.
Get a bunch of students, mostly freshmen, away from home for the first time. Stick them all in a dorm, many of them are armed with a checking account and checks, a credit card, a student ID card, their driver license and Social Security card. It’s a recipe for ID theft.
Realizing that, many colleges and universities, with the help of their banking partners, have incorporated ID theft prevention techniques into their financial wellness seminars.
“We’ve done these seminars for years–how to manage credit, how to make a budget and now we have created ID theft prevention as an extension to financial wellness,” said Whitney Bright, vice president of campus cards for U.S. Bank. “The seminar is popular, not only with students but faculty and staff.”
Campus identity theft seminars popular with both students and staff
That’s a sentiment echoed by Randy Hedge, director of university dining and Reeve Dining at University of Wisconsin Oshkosh. “When the university, with the help of U.S. Bank, held our ID theft program it was absolutely overflowing and at least 60-70 percent of those present were faculty and staff.”
He said it was obvious “people are very sensitive to the ID theft problem. It was an excellent program and U.S. Bank had several of their staff there that day.”
When the university signed with U.S. Bank about three years ago, “they told us they wanted to do as many educational programs as we were interested in having them do. The ID theft topic was presented in their proposal as educational programs they would be happy to present. We will plan to have more programs like this.” ID theft will be just one of programs, “but probably something we’ll do every year along with Banking 101,” he added.
He learned “a dozen different ideas that people should remember not to do. I know one in particular is you shouldn’t use your mailbox on the street to mail your bills.”
“This is another thing we talk about,” said Ms. Bright. “If you’re paying a bill, put it directly into the post office box instead of a college box. It’s very easy to get account numbers off those documents.”
U.S. Bank can either incorporate ID theft into its other seminars or run it stand-alone. “It depends on who the audience is–students, faculty and staff–and how much time we have,” said Ms. Bright.
Seminar topics include protecting your Social Security number, phishing and, of course, what it means. Seminar participants are also bombarded with tips, such as shredding documents (particularly bank statements when you’re done with them), not responding to emails and the fact that “banks will never ask you to verify your pin numbers,” she added.
Of particular use for students living in a dorm are to secure or lock up any extra checks you’re not using. The same measure should be taken for any credit or debit cards that are not in your wallets. “Why tempt someone?” asked Ms. Bright.
Credit card offers are other sources of ID theft. “Hopefully they (students) are throwing most of those away,” she added.
Getting rid of a credit card? Don’t just throw it away, cut it in several pieces and deposit them in different trashcans. “These are all things we talk about,” said Ms. Bright.
She also suggests paying bills online rather than with a paper check. Internet payment sites are more secure, as designated by the “https” at the beginning of the address rather than the normal “http.”
And always go directly to the bank’s Web site. “Start from a fresh Web site and don’t link off another site or off another email. “I have my U.S. Bank site in my favorites so I know it’s going to the right site.”
Another tip: “Don’t carry your Social Security card around with you and don’t have it printed on your check. Most schools today have moved away from having a Social Security number tied to the ID card.”
Higher One educates cardholders online
Sean Glass, Higher One’s chief marketing officer, said the number one protection against ID theft is knowledge, “know what to watch for.
Higher One, said Mr. Glass, primarily provides ID theft information online. For example, the Web site of one of Higher One’s clients, the University of Houston, includes “a box that you can click on to learn how to protect yourself.”
“Most students are pretty savvy (but) preventing ID theft involves understanding how criminals work.”
One of the biggest threats, of course, is phishing, attempting, usually via email, to get the recipient to click on a link that looks like it came from the bank. A related scam involves “attempts to get information through social engineering. You get a phone call from someone saying their attempting to clean up their records.” In essence, such calls are attempts to get any ID information that can help the scam artists steal identities. Social Security numbers are key, but they may also ask for dates of birth, mother’s maiden name, etc.
“We tell our customers that if you get an email that doesn’t look like it came from us, don’t click on the information.”
Since Higher One is an Internet-based financial services provider, it’s important that students, faculty and staff be careful when dealing with any emails from the company. “Don’t assume it comes from us. Go to the URL on the back of your card to log in.”
He said Higher One has not “had many people reporting cases of ID theft.” Regardless, most banks and Higher One follow a zero liability policy “and we’ll work with the student to get his money back in any event.”
But ID theft, he says, isn’t as important as protecting your documents, primarily credit cards. “The number one way a card gets stolen is when it’s skimmed.” That usually happens when your credit card is out of your sight for a few minutes, such as when you’re paying for a meal at a restaurant. The waiter could capture that credit card number and later use it or sell the number. “That’s why you have zero liability from credit card companies,” said Mr. Glass.
“The number one thing is awareness. When something doesn’t seem quite right, it probably isn’t,” he added.
Interactive programs key to Wells Fargo’s student education
Wells Fargo’s Julia S. Tunis, assistant vice president, corporate communications, says the bank uses its web site not only for financial management training but other areas as well, including ID theft.
The bank’s Hands on Banking program (www.handsonbanking.org) “is a free, fun, interactive money management program that teaches the money skills needed for all stages of life. (It covers) ID theft, fraud, phishing/online scams and protecting your credit. In addition, we have published articles in the Student Wells Wire online newsletter about protecting yourself about identity theft.”
She said that Wells Fargo, for all customers, has online content about ID theft at www.wellsfargo.com/privacy_security/fraud/operate/idtheft.
It was just announced that one of the longest standing, leading campus card providers – General Meters Corp. – has been sold to Heartland Payment Systems, a leading merchant payment processor. Heartland is a newcomer to the campus card world launching its first installation of a campus card offering early this fall at Slippery Rock University. The project was notable for making use of contactless payments via tags that affix to student cellphones.
Heartland does have other campus connections, however. It serves as the payments processor for a reported 300 institutions, and the company acquired reader manufacturer Debitek about two years ago. Stay tuned … more details will follow as the CR80News editorial team can reach key players.
HEARTLAND PAYMENT SYSTEMS ACQUIRES GENERAL METERS CORPORATION
Acquisition Allows Heartland to Offer Universities Complete Payment and Campus Card Solution
Princeton, NJ—October 22, 2007— Heartland Payment Systems, a leading provider of credit/debit/prepaid card processing, payroll and payment services, today announced it has acquired General Meters Corporation, a developer and provider of one-card systems for college and university campuses. Financial terms of the transaction were not disclosed.
Founded in 1979, General Meters has grown into a leading provider of campus card solutions for universities and colleges nationwide. Its University One-Card System™ unites a range of functionalities – including security access, on-campus dining and vending, employee record keeping and copier/printer/fax control – onto one ID card for students, faculty and staff.
Adding yet a different kind of functionality to campus one-card systems, this fall, Heartland launched the first university contactless payment system in North America at Slippery Rock University in Slippery Rock, PA. Using either an ID card or a cell phone, students, faculty and staff can make payments at on-campus locations as well as participating off-campus merchants.
“The combination of Heartland’s contactless payments application with General Meters’ University One-Card System will create the next-generation of one-card systems,” says Bob Carr, chairman and chief executive officer of Heartland Payment Systems. “The resultant all-inclusive campus ID and payment system will offer an efficient, cost-effective opportunity for colleges and universities across the country.”
General Meters’ more than 150 clients will be amongst the first to be able to implement this solution.
“Adding Heartland’s technology to the platform our clients already use will take these schools into the future,” notes Leon Gottlieb, founder and chief executive officer of General Meters. “The integration of contactless payments to the existing functionality of our one-card system will not only foster additional convenience and operational efficiencies for these schools, it will also give surrounding off-campus merchants the ability to increase their revenue by accepting university card payments.”
“We look forward to working with our new university clients gained through this acquisition – as well as colleges and universities nationwide – to bring state-of-the-art one-card solutions that improve student service and generate administrative cost savings,” Carr concludes.
About Heartland Payment Systems
Heartland Payment Systems, Inc., a NYSE company trading under the symbol HPY, delivers credit/debit/prepaid card processing, payroll and payment solutions to more than 150,000 small and mid-sized businesses nationwide.
Heartland is the founding supporter of The Merchant Bill of Rights, a public advocacy initiative that educates merchants about fair credit and debit card processing practices. For more information, visit www.heartlandpaymentsystems.com and www.MerchantBillOfRights.com.
Forward-looking Statements
This press release may contain statements of a forward-looking nature which represent our management’s beliefs and assumptions concerning future events. Forward-looking statements involve risks, uncertainties and assumptions and are based on information currently available to us. Actual results may differ materially from those expressed in the forward-looking statements due to many factors. Information concerning these factors is contained in the Company’s Securities and Exchange Commission filings, including but not limited to, the Company’s registration statement on Form 10- K, or Form 10-Q as applicable. We undertake no obligation to update any forward-looking statements to reflect events or circumstances that may arise after the date of this release.
Contact
Nancy Gross
Heartland Payment Systems
888-798-3131 ext. 2202
[email protected]
or
Kristen Forbriger
Gregory FCA Communications
610-642-8253 ext. 167
[email protected]
 When shopping for an ID card printer, you’re liable at the outset to be hit with two choices: direct-to-card or reverse image transfer? Making an informed choice depends on what kind and how many cards you’re trying to print.
When shopping for an ID card printer, you’re liable at the outset to be hit with two choices: direct-to-card or reverse image transfer? Making an informed choice depends on what kind and how many cards you’re trying to print.
Direct-to-card (DTC) printing is the most common technology used in desktop ID systems to print images directly onto the surface of a plastic card. It does this by heating a special print ribbon beneath a thermal printhead, resulting in the transfer of color from the ribbon to a blank card.
With reverse image technology, the printer first prints images onto a special film that is then fused into the surface of a blank card through heat and pressure. Because the graphics and text are printed on the underside of the film, the image is “sandwiched” between the film and the card. This process produces excellent print quality, is durable, and provides the ability to print with a wide variety of card technologies and on many card types.
Both of these printing technologies share two printing methods: dye-sublimation and resin thermal transfer.
Dye-sublimation is the process used to print smooth, continuous-tones that bear photographic-like realism. This process uses a dye-based ribbon that is partitioned by a number of consecutive color panels. The panels are grouped in a repeating series of colors–cyan, magenta, yellow, and black (CMYK)–along the length of the ribbon. During printing, a printhead containing hundreds of thermal elements heats the dyes on the ribbon that vaporize and diffuse into the surface of either the card or the film. A separate pass is made for each of the different color panels. By combining the colors and varying the heat used to transfer them, the printer is able to produce up to 16.7 million colors.
Resin thermal transfer uses a single-color ribbon to print sharp black text and crisp barcodes that can be read by both infrared and visible-light scanners. This process uses the same thermal printhead as dye-sublimation; however solid dots of color are transferred rather than a combination of colors.
When you’re printing contact or contactless smart cards, the “printing technology of choice” is reverse transfer, says Fargo’s Steve Blake, vice president of product marketing.
Why? Smart cards have embedded chips. “Anything with electronics embedded in the card doesn’t always end up with a flat surface. A dye sub process … creates some issues (with print quality). By printing to reverse transfer film instead of the card surface itself, you have none of those problems. It’s very forgiving with electronic cards,” said Mr. Blake.
The dye sub process is also known as direct-to-card printing. As Mr. Blake explained it: the ribbon comes in direct contact with the card. “If you have a contact chip in a smart card, that chip is supposed to be flush to the card, but that’s not always the case. There might be a little ridge or bump and if the printhead contacts the chip on the card, it can blow a pixel out (on the printhead).” Then you have the costly problem of a damaged printhead that, in many cases, costs about half (or more) of the printer’s original purchase price to replace.
What’s more, a DTC printer can leave blotchy white spaces around the chip. You therefore end up with a bad card that you “have to throw away. That might be a $4 card so you’re damaging an expensive inventory item,” he said.
Reverse imaging technology, “really doesn’t care whether the card is smooth or not because the printhead is contacting the ribbon which contacts the film. The film is then attached to the card in a single pass through the printer,” said Mr. Blake. “The film can produce a much better image, the colors are truer, you have a higher resolution and a crisper, cleaner, truer look. It resembles a preprinted card that you get from a card manufacturing plant.”
Reverse imaging also makes it easier to produce secure cards equipped with a hologram. “Historically, holograms had to be put on by a lamination module attached to the printer,” explained Mr. Blake.
But reverse transfer film can be produced with an embedded holographic image. “You don’t need a laminator module. This is wonderful news for the middle and entry level (organization).”
“With smart card growth, people are telling us more and more that they want that high definition printing technology, but at an affordable price,” Mr. Blake said. Reverse image has become the technology of choice for both its superior image quality and its ability to print high-quality images on contact and contactless smart cards. In most cases, these printers cost more than their direct-to-card counterparts, though many printer professionals suggest that reductions in the total cost of ownership outweighs the additional upfront costs.
 By Andy Williams, Contributing Editor
By Andy Williams, Contributing Editor
Providing campuses with the ability to instantly notify their students in the event of a disaster or emergency was on most campus card vendor’s to-do lists. But the Virginia Tech incident quickly moved what had been a mid-tier suggestion all the way to the top.
The deadliest shooting in U.S. history occurred April 16, 2007 when Seung-Hui Cho killed 32 people and wounded 25 others before killing himself on the campus of Virginia Tech in Blacksburg, Virginia. Since then, colleges around the country have been investigating ways that students, faculty and staff could have been notified quicker.
Tasked with the need to develop a system that can get emergency messages out quickly, campus card and other technology providers have been investigating what’s available and what needs to be done.
Since a cell phone today is like a third appendage to most students, the most obvious solution is an instant messaging service that would notify students within seconds of a possible disaster or “gunman on campus” type of scenario. Easier said then done, however. Not only do you need every student’s cell phone number, whatever system you use has to be compatible with numerous mobile phone carriers–not just the AT&Ts or Verizons, but the smaller ones as well.
“This is one of those projects we had on the list to do,” said Niles Dally, vice president, sales and marketing, for NuVision Networks’ One Card System. “We’ve been looking at it (emergency notification) at various times but with the advent of Virginia Tech, we pretty much decided this is something we really needed to implement immediately. It’s now in our testing facilities in Lebanon, PA.”
“Pages, cell phones, emails and other systems are all being investigated,” said Jeff Zander, vice president of campus card provider General Meters. “We’re looking at the capability of sending pages to alphanumeric pagers, any device they (colleges and students) want to register.”
“You would have been hard-pressed to find a college with any organized, documented notification system in place before April 16,” Read Winkelman, national sales manager, colleges and universities for Ithaca, NY-based The CBORD Group, which serves Virginia Tech, commented.
CBORD had a number of planned enhancements pushed to the front burner after the Virginia Tech shooting. “We had the concept for it brewing a couple of years ago but other things came to the forefront. We react accordingly to the requests we get from our customers and we only had one actual comment about this in the past. After Virginia Tech, we got a few more,” said Mr. Winkelman.
“It’s a tall order which requires a tremendous amount of buy-in from administrators, parents, and especially students,” adds Mr. Winkelman. “What we have been focusing on is a dialogue with customers, and looking at existing and potential access control and electronic security products, cameras, etc.”
Text messaging powers instant alert networks
Perhaps the most obvious choice for rapid student notification is cell phone-based instant messaging.
“The single biggest challenge for something like a text-based message for cell phones,” said Mr. Winkelman, “is getting the cell phone numbers. Institutions need to encourage students to provide this information and for parents to get on board. It will probably never be 100%, but you’ll see that more and more students will supply their emails and cell phone numbers.”
That’s the problem with any text messaging service. Should students have the option of providing their cell phone numbers, or should they be required? “I would urge the university to make it mandatory,” said Mr. Zander. “It shows that this institution will do everything in its power to make sure students are safe. We’re not using it for marketing or promotions. It’s a threat alert system and won’t be used for any other purpose. It should be the university policy. The student should not be able to opt out.”
 He said a General Meters’ campus “can have an unlimited number of contacts for the individual. If the student is hearing impaired, you could send the message to the parent who could then contact the student.”
He said a General Meters’ campus “can have an unlimited number of contacts for the individual. If the student is hearing impaired, you could send the message to the parent who could then contact the student.”
At a few CBORD campuses, presidents have already contacted parents to encourage them to have their sons and daughters share their cell phone numbers with the university. This, said Mr. Winkelman, would fall under the heading of: “We’d like to have a way to contact your students in an emergency situation.”
Mr. Winkelman said CBORD isn’t “promoting a school-wide messaging service at this time. You’d see the message on a POS terminal, etc., but it wouldn’t go to your cell phone. We are currently exploring options for text messaging on cell phones.”
Mr. Zander said General Meters “currently offers a number of automated features to broadcast select responses or other time sensitive security information. This includes alphanumeric pagers, cell phones, email, and a myriad of text messaging options.”
Messaging is available to all students at a General Meters-supported school, via the General Meters OneCard, but an expansion is planned “to allow multiple cell phones, emails, or text messaging. From a central system, a security officer could key in the code and send it one time and it would run through the database and hit all these people. We hope to have this completed in 2007. The ability to alert security personnel is available today. We’re going to take it to the next level and staff would physically type the information that will be sent out to the students,” he added.
He explained that when a student sets up a General Meters account, his information is fed into a database that can then automate delivery to his cell phone, email, etc. From that the college can also broadcast to a number of devices including a fax machine. Any device that can receive a communication, even a landline telephone, is eligible, he said.
He calls this an automated threat alert response, automating the alert or indication of a possible breach of security. “Let’s get everyone the notice. Or at least everyone who signs up.”
The system will include pull-down menus covering all the wireless providers, Verizon, Cingular (now AT&T), etc. “Let them select their carrier because not all text messaging systems are the same,” he added.
“The client (the college) should be able to determine how to alert its students, whether by group, text message, cell phone,” he said. A sample message could read: “Lock-down, security breach, assailant unknown, please stay in your room.”
“It should be sent by a security officer but anyone with access to a keyboard could do it … but we’re reserving it to security officers only. It could be sent to every device registered to that student. For example, all card holders could receive a message instructing them to remain in their dorm rooms,” he added. “We would have to have the cell phone or pager number or the email address.”
NuVision’s emergency notification system will be piggy-backed onto the company’s existing One Card System known as iAMECS Advanced.
NuVision’s messaging system uses the iAMECS Advanced SQL Server databases to provide the right messages to the appropriate individuals. “iAMECS is installed at the college, not at a remote location,” said Mr. Dally. “This is important because it’s under the control of the college. Someone there doesn’t have to call an off-campus location to get the messages out to students. ”
He said the new service will provide messages in three tiers.
“Tier 1 is an emergency message, which would be a major incident on campus,” said Mr. Dally. “Based on that, you can send text and email messages to select groups of people, for example a specific dormitory. Or you could text message the RA (resident assistant) to get people out. Or you could text message all people in the dorm, telling them to get out. You can break down messages anyway you want. Notification is virtually instant. It all can be handled on campus. No one needs to email a third party. It’s based on demographics in the database, which has almost always been populated by the Student Information System (Banner, Peoplesoft, Datatel, etc). ”
Tier 2 would be priority, not necessarily an emergency message, like the area is subject to severe thunderstorms or, the school is closed today, he added. “Tier 3 would be a general broadcast, like there’s a rally for the football team.”
He said there’s no message limit. Minimal fees will be assessed per cardholder per year. “We’re hoping to have a beta this fall in one or two colleges. It then will be available to all clients after that. We will need to have cell phone numbers of cardholders. Those numbers need to be in the database.”
It will have a web interface that allows students to manage their accounts. “We call it the Campus Center. There will be a page that allows cardholders to enter their cell phone numbers. We have the communication protocols for all the different systems. That’s what the beta is for … to find out if there are any systems out there we don’t know about,” said Mr. Dally.
“We also have to know the cell phone carrier. The Campus Center will have a page to allow the cardholder to inform us of that info or inform us of their changes when they change carriers. Any marketing campaign (offering special discounts and the like) can be used and if you tie this in you’ll have more people sign up,” he added.
He said the system can be installed “in a couple of days. We can do video training if necessary. This is all part of the beta testing.”
He said some colleges have similar systems, but they’re hosted off campus. “The beauty of our system is that anyone can handle it. We know it’s going to work, electronically, mechanically, but logistically, that’s the crux of the thing. How do we get it set up? How do we set up the notices?”
Another problem is “what message do we send out? If we say there’s an armed individual and you should exit the building, where do you exit to? Or maybe there’s an armed individual last seen at … It needs to be something fast. And the only way is to have it hosted on campus.”
Campus lockdowns
There’s another way to secure the campus: don’t let anyone in or out except emergency personnel.
CBORD offers two major campus card technology platforms: CS Gold® and Odyssey PCS™. While Odyssey PCS did not originally have any door access functionality built into it, the system interfaced with other technologies. According to Mr. Winkelman, “when we acquired CS Gold (from Diebold) we integrated its CS Access™ component with Odyssey PCS. This and other security features have had major areas of focus for the last couple of years.”
Since then, CBORD has been working on “an enhanced lock-down capability for online locks that can be handled from one source, such as a computer terminal in the security office,” said Mr. Winkelman. There would also be an emergency capability for offline locks that could be activated with the swipe of a card. But in this instance college personnel, such as a security guard, would have to physically visit each door to lock it.
 POS notification
POS notification
Another method campus card providers are exploring is utilizing online terminals to get the word out. “Universities have terminals all over campus–vending machine readers, POS readers, etc.–that make it easy to display certain patron messages at the time of purchase,” said Mr. Winkelman. “We can create an emergency message to display at the beginning of the message (on the transaction slip) that is delivered at the time of sale. We can also set the emergency message to display when terminals are idle. So when the readers aren’t in use, the message can continually flash across terminal screens,” he added.
This could be used in the event of inclement weather, natural disasters, or criminal activity – it could be a tornado warning or a message to check the campus web site. “You would get that message when you pay for a tray of food, for example. The message would come at the end of the transaction or, when you buy a Pepsi from the vending machine,” added Mr. Winkelman.
But this should not be the sole means of getting the word out to students. It is one mechanism used to augment schools’ other notification engines,” he stressed.
Like CBORD, General Meters has proposals in the works that would revolve around POS devices. Mr. Zander said the company is “currently investigating a number of other technologies that will provide automated threat response messaging enhancements. As an example, this would include sending a message to certain card readers and/or POS devices. When a card is swiped it would say there is a security concern and that the cashier (and student) should go to a certain location,” he added.
Or it could be as simple as alerting a student this his chemistry book is waiting for him at the bookstore. “You can send messaging of any nature to anyone who has a card. A text message could be dropped onto a directory that could be sent to every student. If you don’t carry a cell phone, you might have a pager or email. Ideally, you would want to use at least two or three methodologies. That way, we could double up to assure that the message gets delivered.”
What to do in the event of…
CBORD is continuing to talk to its customers about what they’d like to see, said Mr. Winkelman. “We’ve done webinars to get some feedback from our clients. We’ll also be having sessions at our user group conference on disaster preparedness or other emergency situations that might arise on campus, whether weather-or people-related. There are many bases to cover and questions to ask. For example, if the campus loses power, what happens to security? And if you need to have a lock-down, how do you control it?”
One of the latest webinars CBORD held with its customers was to let them know about new security features of CS Access, including the enhanced lock-down application, an emergency access plan category, messaging on CBORD terminal devices with displays (vending readers, POS devices, some types of door readers), and integration of housing assignments and access plan assignments. “The terminal messaging is just one of the features we are rolling out as part of an effort to improve our already robust integrated security solutions,” added Mr. Winkelman.
He said customer feedback to the webinar “was very positive,” but emphasized that these were sessions CBORD already had in the planning stages and were not a reaction to the Virginia Tech situation.
After the Virginia Tech shootings, Mr. Winkelman said CBORD “quietly provided our contacts there as much assistance as they needed. Anything we could do to help. After it happened there really wasn’t a lot for us to do other than some database queries they needed us to make that weren’t standard reports. So we built some custom reports for them. They did have a lock-down procedure. The doors were controlled by CS Gold.”
As is obvious, a perfect text notification system probably isn’t available yet. One system not mentioned is old-school technology … word of mouth. “If you have five people standing there and three cell phones go off simultaneously, you’ll never get everyone but those two without cell phones will still get the message,” said NuVision’s Mr. Dally.
“Generally, though, those without cell phones will receive emails,” he added. Another suggestion, he said, has been to implement a reverse 911 system, “where students actually get a phone call (on their landline). The problem is there is no methodology that one instrument can dial out to multiple phones instantly. You would need to have a bank of phones dialing out,” he said.
It seems there is no perfect solution to instant student notification, and even if there was it is unlikely to stop a tragic event from occurring. The goal can only be to minimize the extent of the damage through rapid communication.
German printer manufacturer Digital Identification Solutions has added a series of new products and a major new security initiative to its line of card printers. In addition to 10 new products, the secuirty additions include three important changes: Security Erase to eliminate the remnant data from the black panel of the printer ribbon, IPSEC for encrypted data transfer in the network, and UV printing for invisible security printing.
New Security Features Available with the EDIsecure® XID 5xxie Retransfer Printer Family
Stuttgart, Germany, 18 September 2007 – Digital Identification Solutions AG (A0JELZ), a worldwide leader of identification solutions, has announced a number of new security features for the EDIsecure® XID 5xxie Printer Series, unveiled during the company’s most comprehensive product launch program since its foundation, involving a total of 10 new products.
The German-based Digital Identification Solutions Group has set up the new EDIsecure® XID 5xxie Printer Series with a variety of security features, helping to secure the customer’s application and cards from counterfeiting and to avoid misuse of personal information. All printers are equipped with the new security features Security Erase and IPSEC, the two models XID 580ie and XID 590ie possess in addition a revolutionary dye-sublimation UV ink ribbon for printing invisible information on demand, as well as creating monochrome photographs with a special dithering technology, which provides for high quality black & white images, e.g. on the rear side of a card.
Security Erase of printed black data on used supplies helps to protect from misuse of printed personal information. Immediately after card printing all remaining information on the K-Panel of the ink ribbon is erased, so that the personal information cannot be reconstructed out of the used supply. The printed information is not readable any more from the K-Panel. This feature increases the security enormously, especially in environments without secure disposal of used supplies.
IPSEC allows encrypted data transfer through the network. IPSEC (IP security) is a suite of protocols for securing network and internet protocol communications by authenticating and encrypting each IP packet in a data stream. A big advantage of IPSEC is that security arrangements can be handled without requiring changes to individual user computers. It also includes protocols for cryptographic key establishment.
The new security feature UV Dye-Sublimation Ink enables the utilization of “on demand pictorial printing” of invisible photographs, logos, emblems, symbols, coats of arms and even variable text. This revolutionary UV printing technology allows finest tone scale reproduction for personalization of invisible photographs of highest quality. The printed UV information is not visible to the naked eye, but can be verified easily by using a UV light source. It is therefore a fantastic and attractive security feature for corporate and government clients.
The monochrome dithering process allows customers to print high quality black & white photographs even on the rear side of a card, without the need to use another set of YMC color fields. Therefore the security of a card can be increased in on the rear side without increasing the printing costs.
The group will introduce the new program to the public at more than 17 international trade fairs, exhibitions, VIP events and web-casts within the next 3 months, therefore reaching all customers around the globe. Further details about the security features available with the new EDIsecure® XID 5xxie Retransfer Printer Family are available on the company’s website www.digital-identification.com.
About Digital Identification Solutions
The Digital Identification Solutions Group is a global provider of advanced identification solutions with a worldwide installed base of more than 5,000 systems. In September 2007 the Group has introduced the latest EDIsecure® XID 5xxie Retransfer Printer generation successfully into the world market. The company has sales, marketing and support operations in Europe, the Middle East, Asia, Mexico and the United States. Together with its vast network of certified partners, Digital Identification Solutions is in a position to deliver state-of-the-art solutions virtually anywhere in the world. The company combines cutting-edge technology, extensive industry know-how and an impressive array of references in the private and public sector.
For further information please visit www.digital-identification.com
Leading payments processor, Heartland Payment Systems, joins the ranks of campus card providers

By Andy Williams, Contributing Editor
Contactless technology is coming to the 8,600-student strong Slippery Rock University in Pennsylvania. But it won’t be a card. It’s coming via cell phone, thanks to a small tag not much bigger than a postage stamp.
When Slippery Rock’s students arrive for classes this fall, they’ll be greeted with a new campus card and an accompanying 13.56MHz contactless token designed to stick to the back of any cell phone.
Both tag and card are being delivered by Heartland Payment Systems, the sixth largest payment processor in the world. It has been processing Slippery Rock’s credit and debit card transactions for the past 10 years, so it seemed a natural fit when the university decided it wanted to introduce a new technology for the college’s campus card. Dr. Robert Smith, the university’s president, wanted to involve the cell phone in the new program because of its ubiquity among students.
Barry Welsch, manager of IT priorities for Heartland and the project manager for the Slippery Rock implementation, is also vice chairman of the SRU Foundation Board. He recalled that one day Dr. Smith, “wrote me a letter asking if I knew of any products that could make their current on-campus Rock Dollars program (the university’s declining balance program) more robust” while enabling off-campus merchants to accept the card.
As Dr. Smith explained later: “We want to leapfrog the current technology and go to the cutting edge, and we want to add value to our student’s experience at Slippery Rock. We believe this is the future and want to be educators of our students in the management of this technology…to take a responsible role in helping them learn to manage it.”
Once the scope of the initiative was developed and deliverables were identified, the university solicited competitive bids from a variety of potential vendors. With its advanced technology and visionary approach to the future of campus payments, Heartland earned the right to be Slippery Rock’s exclusive provider of this service.
Dr. Smith added: “We needed a partner who was courageous enough to bring it to the U.S. and work with us on the introduction of this application. We knew we couldn’t do this by ourselves, and frankly, there wasn’t anyone we could have more confidence in than Heartland to do this for us.”
Mr. Welsch consulted with Heartland’s chairman and CEO, Bob Carr, and the two decided Dr. Smith’s request was very feasible. “He (Dr. Smith) wanted to leap past the current mag stripe technology … and give students exposure to new technology they will be seeing when they leave the university. He also wanted to raise the image of the institution,” said Mr. Welsch.
“It was Mr. Carr who suggested contactless,” said Mr. Welsch. “We talked about using the cell phone as the access device because it’s the most commonly carried item by far.”
A student focus group drove that point home. “We asked the students several questions: ‘How many of you have at least one dollar in change in your pocket?’ Only four of about 50 in that group had at least a dollar,” recalled Mr. Welsch. “About 75% had their student ID cards. But every single student, except one, had a cell phone. And that student had lost his the day before. It was very clear to us that a cell phone goes with a student everywhere. Mr. Carr told me later that students know they’ve lost their cell phones four times quicker than if they’ve lost a wallet.”
To make this happen, the most obvious choice would have been near field communication, a technology developed several years ago by chip makers NXP and Sony that gives cell phones RFID capability, allowing them to be read by contactless readers. But the technology is still new, and not yet widely available in the U.S. So Heartland went the next best step: producing contactless-enabled tags that can be affixed to the student’s cell phone.
Why tags? Heartland and SRU got some reinforcement for this decision from the same focus group. “Another thing quite interesting we learned,” said Mr. Welsch, “is that students said when they visit with family members and friends and someone pulls out a credit card branded with a university name rather than a vanilla Visa card, they felt envious. Students were really excited about the fact that students from other universities won’t have this. President Smith loved this idea.”
How does it work?
So, students, faculty and staff this fall – about 10,000 of them in all– will be receiving a half inch wide by 1.5 inches long contactless token with a strong adhesive backing they can attach to their cell phones. It then works like any contactless card, meaning that it can communicate with the reader without physically touching it. The readers have lights that indicate whether the tag is being read or not.
“We tested it on the outside of the phone, and you can scan within an inch and a half. When inside the phone, you need to be about an inch closer,” said Mr. Welsch. He suggested that some students may want to remove the phone’s battery cover and insert the tag there.
If a student changes phones, he can remove the tag and reattach it to the new phone. If the tag won’t come off, the student can apply for a new tag.
The tag “has a very durable exterior. It can’t be scratched, and it seldom will show signs of wear,” he added.
Heartland is also issuing new student ID cards since the company will, for the first time, be processing the student Rock Dollar accounts. Before, Heartland processed only the traditional credit and debit charges students and parents use to pay tuition, room/ board and buy books, Mr. Welsch said. “We’ve not had anything to do with Rock Dollars. It’s something the university has maintained on campus with proprietary readers and terminals.”
The Heartland-issued ID cards, however, are still equipped with mag stripes rather than contactless chips. Dual technologies mean making sure the university has readers that can handle both. “Everything we’re building – the laundry, vending machines, merchant-attended POS terminals – all will have readers that can read the contactless token” as well as the mag stripe cards,” Mr. Welsch continued.
“As far as we can tell, this dual technology is unique. It’s the first application in a higher education institution in the U.S. to go this way.”
Once the new cards are issued, Heartland will transfer the old Rock Dollar balances to new accounts. In this manner, students can seamlessly migrate from their prior cards to the new system without losing deposited funds or having to maintain two accounts.
“On Track Innovations (OTI) is supplying the tags, and we manufacture the readers through our micro-payments division,” said Mr. Welsch. That division includes longtime campus card reader manufacturer Debitek, a company Heartland purchased in 2005. “Heartland has re-engineered the (Debitek) technology,” added Mr. Welsch, “bringing it up to state-of-the-art.”
 Taking Rock Dollars off campus
Taking Rock Dollars off campus
The second phase of the project is recruiting merchants off campus to accept Rock Dollars. Initial reaction has been positive, reported Mr. Welsch, stressing it’s a winning combination for both the university and the merchants. The university doesn’t have to process merchant accounts or cut them checks, and merchants get paid daily.
To no one’s surprise, the first merchants to sign up were restaurants. “We’re also looking at supermarkets, retail clothing stores, a shuttle service and nail salons,” said Mr. Welsch.
Before, merchants were paid monthly. There were no off-campus merchants, but still, the on-campus bookstore and foodservice providers had to wait for their money. “Under our system, we process the transactions nightly and generate an ACH deposit to them the next day, exactly the same time as credit card (payments),” he said. Merchants can purchase or rent terminals, starting at $25 a month. The transaction fee varies depending on the amount of the purchase, but averages about 1.5%, plus 25 cents per transaction.
“We do not use proprietary terminals,” noted Mr. Welsch. “The merchants like that. They only need one terminal to accept credit, debit or Rock Dollars.”
Dr. Smith said the most “perplexing problem” has been the university’s insistence to provide greater protection for the students by requiring a PIN when they use their contactless tokens. That’s not something merchants usually expect from someone paying with a debit card, specifically at restaurants. “This is creating a challenge,” added Dr. Smith.
For on-campus use, that’s not an issue since all vendors have a PIN pad. But some off-campus merchants don’t currently have a PIN pad. Mr. Welsch said Heartland hopes to have this problem alleviated shortly. Heartland’s readers/terminals all have PIN pads, but, said Mr. Welsch, there are also other packages available that include PIN pads merchants can use. Bottom line: If a merchant wants the student’s business, he/she will need to be able to accept a PIN as part of the transaction.
For smaller transactions, such as those performed at vending machines, no PIN is required.
 Managing your account on the web
Managing your account on the web
Another advantage to Heartland’s program is that students can go to a web site to check their balances or their transaction history, said Mr. Welsch. The web site option is new. Before Heartland’s involvement, students could only utilize a reader to find out their balances.
Students who lose their cards or tag-enabled phones can visit the same web site to get their accounts frozen until a new card and tag can be issued. They can also contact Slippery Rock’s card office and receive support through a toll-free number. “The web provides 24/7 access for cardholders and doesn’t limit students to having to visit the administrative office during normal business hours to have a freeze put on their accounts,” said Mr. Welsch.
“One of the other great features isn’t so much contactless but the whole web-enabling structure,” added Dr. Smith. “The individual can review his/her account and charges – as well as reload the card from the web or via phone. It’s more than just a chip. The whole concept is somewhat revolutionary for us.”
All accounts are maintained in an FDIC-insured bank, Mr. Welsch emphasized.
Changing the way financial aid is delivered to students
Another big change is the way students receive financial aid. “Nearly two-thirds of Slippery Rock’s students are the first generation (in their family) to go to college, so financial aid plays a big part,” said Mr. Welsch. “When financial aid comes in now, the university will take out tuition and room and board and distribute the excess to students.”
In the past, this excess was distributed by check, but now that money can be direct deposited into the student’s Rock Dollars accounts. “We’ve gotten quite a few calls from students already excited about the new system,” said Mr. Welsch. “All that’s been released has been the financial aid form with a new check box allowing for the money to be direct deposited.”
Additionally, on- and off-campus paychecks can be deposited directly into the same account.
Giving something back
Another feature involves charitable giving. Remember that 1.5% transaction fee merchants have to pay to accept the student’s Rock Dollar card or contactless token? Heartland doesn’t profit from it. The money goes back to the students or the charity of their choice.
“We are rebating back to the students through the Give Something Back Network,” said Mr. Welsch. Students will be able to go online and select their favorite charity to have this money donated to or they can have it credited to their own account.
“That’s another important feature about our system that the university liked. Universities struggle to get their students to give something back down the road when they become successful. Slippery Rock is trying to build that thinking in their students. The Slippery Rock Foundation will be listed as the first charity they can donate to. Students will at least see the concept of giving back.”
A new player in the campus card market?
Mr. Welsch hopes Slippery Rock is just the beginning for Heartland in the campus card business. “We’re looking at doing this at other universities. It will be a product offering under our campus card product line” in the company’s micro-payments division. The company, which is traded on the New York Stock Exchange, provides credit/debit/prepaid card processing, payroll and payment services to 150,000 merchants – including restaurants, hotels, and retailers – and 300 colleges throughout the U.S.
What will determine whether Slippery Rock University’s card program is successful or not?
“We’re going to judge it by the number of merchants we sign up. Obviously we also want to sell them credit/debit, and payroll processing – as well as remote check deposit services,” said Mr. Welsch. “We will judge the success of this project on the merchant participation and the future of selling or renting additional readers to the university.”
Dr. Smith likes what he’s seen so far. In fact, he has been a guinea pig, of sorts. “They gave me one (a contactless tag), and I’ve gone around using it. Since it was Heartland’s money on an experimental card, I had a great time,” he laughed.
“We’re going to see where this goes,” he added, “but from a branding standpoint, we couldn’t be more thrilled. Heartland is out there encouraging all these retail establishments to accept these Rock Dollars, and the merchants are signing up. That means they’re looking for a Slippery Rock patron.”
He said the contactless tag concept has also created “quite an international buzz. This kind of reputation for us is, to borrow the MasterCard line, ‘priceless.’”

