 Keeping track of the bad cards–those that were printed but never issued–is just as important as tracking the good cards when managing your ID card system.
Keeping track of the bad cards–those that were printed but never issued–is just as important as tracking the good cards when managing your ID card system.
For John Ekers, Fargo Electronics’ director of product marketing for software and services, it has become something of an evangelization issue.
“One of the things we’ve been trying to promote, which comes from working with security bureaus, is that it’s not just about your cards, but about your duplicates as well, your bad cards and how you are managing those,” said Mr. Ekers.
 “…particularly in the ID market with desktop printers, you see a huge gap. No one is managing the bad cards, the ones that had to be remade,” he stresses. “Not many have software in place to tell you we made four copies of Jane’s ID badge and the fifth is what we sent out.”
“…particularly in the ID market with desktop printers, you see a huge gap. No one is managing the bad cards, the ones that had to be remade,” he stresses. “Not many have software in place to tell you we made four copies of Jane’s ID badge and the fifth is what we sent out.”
What’s needed is something that will help organizations to do a reconciliation to match bad cards against the inventory and produce an audit trail. “The bad cards don’t necessarily have to be kept on file, but a supervisor needs to look at them, check them off (that they actually reviewed them) and then the cards can be destroyed,” said Mr. Ekers.
It’s all about hardening your security. The card may not have been encoded yet, but the picture is still there, the name is on the card and it could still be used fraudulently.
Fargo and others have tools that can secure the issuance process. “We’re trying to manage the issuance of both good cards and bad cards,” explained Mr. Ekers.
A recent presentation at a National Association of Campus Card Users (NACCU) conference on the issuance process ended, “with most of (the 40 college attendees) wanting to get back to their offices as soon as possible,” said Mr. Ekers. “These were people who initially felt their offices were pretty secure,” he said. “You need to know who has access to your card issuance system. Can someone come in over the weekend and produce fraudulent cards? And what is your liability if that happens? Fear drives a lot of this.”
If you’re providing a system to manage access, but you’re not managing the security of the issuance process, you could still be liable for any breakdown that occurs, he said. For example, someone could print out a fraudulent card that allows him to gain access to a secure building.
One preventative measure organizations can take is to utilize a tool that can lock down their printers. “If you have an application running on your PC, the only way the printer will work is if you present the printer password. That’s more widely accepted in the education market. In a lot of cases,” said Mr. Ekers, “you have students doing the badging process. At least over the weekend no one can come in and access the printer.”
Complementing that system, he added, would be a notification application. “An individual who comes in over the weekend who wanted to print badges and if the printer wasn’t locked up, the printer would send out a message over the network or cell phone and let the manager know that someone is trying to print something,” said Mr. Ekers.
Another possible security gap is the data itself that’s used to print the badges. “We recommend that you don’t maintain that data any longer than you need it. If you look at Visa or MasterCard, they’re not allowed to maintain account information for more than seven days. You don’t have to maintain a local database,” said Mr. Ekers.
Computer advancements have also led to more security holes. The simple USB port provides quick access to data on the computer. “A lot of corporations are not buying computers with USB ports,” he said.
Even if you don’t have the means to implement a sophisticated issuance security and card inventory system, “you can at least have an Excel spreadsheet where you log in the number of cards, cards you’ve printed, and so forth,” said Mr. Ekers. “You really need to manage that inventory.” Or, you could go low-tech with a simple pencil and paper method, he added.
“So many colleges today seem to be overwhelmed with operational requirements. Historically, they’ve let a lot of these things go just to get the cards out the door. But I think they’re starting to understand that there’s a lot more at stake,” said Mr. Ekers.
 Part of the AVISIAN Publishing Expert Panel series to be published throughout December 2006
Part of the AVISIAN Publishing Expert Panel series to be published throughout December 2006
Kathleen Phillips, Vice President, Sales and Marketing
Fargo Electronics
While the implementation of HSPD-12 has been the card-related news to watch in 2006, its effects will be felt in other areas as well throughout 2007.
HSPD-12 mandates the badging of all federal employees and contractors under guidelines formed by the National Institute of Standards and Testing. While this is a landmark move for the federal government, the impact of established standards for smart card credentials on state government, university and corporate markets will have a more far-reaching effect.
For the first time, mid- to large-card program managers have a comprehensive template to guide them in designing and implementing a secure smart card credential program. The NIST standard provides all the criteria program managers should evaluate when creating their programs. While not every feature of the NIST standard may fit their individual programs, the standard provides a thorough checklist for consideration.
Two highlights of the NIST standard are important for other markets:
The impact of the NIST standard, in combination with more readily available, off-the-shelf smart card software applications and overall lower technology card prices will make a higher-security smart card program more reachable for mid to large corporations, state agencies and universities.
And while HSPD-12 was conceived to address security issues, the impact of productivity and efficiency will be seen in applications such as local area network logon, email signature, Web portal usage, etc. Market leaders who demonstrate a return on investment to private sector customers will see a higher adoption rate of their smart card solutions.
 Acquisition brings personalization to HID to “complete the identity management equation”
Acquisition brings personalization to HID to “complete the identity management equation”
By Andy Williams, Contributing Editor
HID Global’s president and CEO, Denis Hébert, calls it “completing the equation.” That’s one way of looking at the company’s recent purchase of Fargo Electronics because it now gives the company a firmer hold on the complete credential management process, from creation to issuance.
Asked about the importance of this acquisition, Mr. Hébert said, “One of the key factors in our decision to make the acquisition was Fargo’s ability to complete our offerings in supplying credentials and ID devices to customers overall. It’s one thing to manufacture them and another thing to personalize them.”
“We saw an opportunity to complete the identity management equation by joining HID’s manufacturing of credentials and Fargo’s ability to personalize the credentials,” he added. “By combining our technologies with their processes, we are able to provide a more complete solution.”
California-based HID Global, a leading manufacturer in the access control industry, finalized the acquisition of Fargo Electronics, an Eden Prairie, Minn. company, in early August after meeting regulatory approvals. Fargo develops secure technologies for identity card issuance systems, including card printer/encoders, materials and software.
Similar cultures, similar missions
“With the completed acquisition, we are now positioned as a leader in the rapidly-growing market for secure issuance of corporate and national ID credentials,” said Mr. Hébert after finalization of the purchase. “Controlled access to materials, intelligent hardware that notifies authorities of misuse, and other enhanced process security features will set a new standard for performance in the industry.”
Mr. Hébert described the long-standing relationship between Fargo and HID: “When we saw the opportunity to merge the two companies, things moved relatively quickly,” he said. Both are now part of the ASSA ABLOY Group based in Stockholm, Sweden.
“One of the nice things about the two organizations is that we’re similar in culture,” said Mr. Hébert. “This is not a scenario of trying to fix things. We’re both well-respected brands working in the marketplace.”
What caught HID’s eye was the fact that Fargo has successfully transitioned from an equipment provider to a solutions provider in the past 18 months by actively addressing the end-issuer’s need to tighten the credential process. This fits nicely with HID’s approach to offer a secure, integrated identity management solution.
One of Fargo’s offerings that addresses the card issuance process is its SecureMark® Technology, which integrates and enhances the security and functionality of the Fargo Card Identity System. Combining hardware and security software, SecureMark is designed to lessen a card identity system’s vulnerabilities by reducing the risk of counterfeiting and unauthorized issuance of cards.
Locking down the card printing process
Fargo’s secure software suite can also protect against unauthorized users printing ID cards. The software tracks who printed the card and when. Last year, the company introduced a hardware aspect of its security system that protects the printer and the materials. SecureVault™ is a physical safe that can house cards, special inks, and other card-making materials.
“We’re trying to provide a closed loop around the entire issuance process from storing blank ribbons to password-protecting printers. SecureVault is an ID management system that controls and protects a critical and often overlooked part of an issuer’s card identity system … the materials,” said Mr. Hébert.
Put another way, he said, “We have a more seamless solution. If I have the ability to program a printer (which Fargo offers), I can provide a better service for end users.”
Does he anticipate changes at either organization?
“There are no real changes anticipated from an organizational perspective. Fargo has been very successful at building its brand and is a well-recognized player in the printing environment, while HID is well recognized in access control, both physical and logical, from a card and reader perspective,” he said.
“Fargo’s experience is with photo IDs and it will continue catering to its channel,” he added. Yet, while both companies, “follow different channels, there are also some areas we can explore together.”
Looking to government, university markets
Moving forward, Mr. Hébert said Fargo will continue to conduct business as an independent unit within HID Global and “both companies will work together to solidify potential synergies and identify opportunities for future digital identity and managed access solutions. The aim is to provide a unique value proposition for high security credential issuance and applications, from process to verification to authentication.”
In the post-merger arena, he sees “some great prospects for both of us. Clearly, both the government and university markets are keenly aware of the issuance process and are migrating towards technology cards. On the university side, there are tremendous opportunities to have more encompassing solutions.”
While the university market has been primarily based on mag stripe cards, from physical access to library management, “the future opportunity is to move towards smart cards and a more decentralized environment, producing more intelligent cards with greater capabilities,” Mr. Hébert said.
At the federal level, with HSPD-12, the issuance process again takes center stage. “It’s a large portion of credential management and what Fargo can produce in the physical and logical access areas melds nicely with HID’s capabilities,” he added.
Government business is, obviously, an important one for both Fargo and HID. Both companies have FIPS 201-compliant products in their lines.
Mr. Hébert foresees federal credential standards being adopted at state and city government levels. “We’re likely to expand into state and municipal governments as well as the commercial arenas,” he said.
For now, both companies are content with adding to an equation in which the whole is greater than the sum of the parts … and one that could result in great opportunities for both companies.
 Some of the contactless world’s best new products were on display at the HID Partner conference in San Diego in October. On display were at least thirty contactless offerings from companies around the world. HID Connect, the company established to help partners of HID Global in their efforts to bring supporting products to market, held their iNNOVATION awards competition. Winners included products that enable wireless physical access control, converge physical and logical access, identify a vehicle and its driver at long range, and facilitate easy creation of contactless applications and products.
Some of the contactless world’s best new products were on display at the HID Partner conference in San Diego in October. On display were at least thirty contactless offerings from companies around the world. HID Connect, the company established to help partners of HID Global in their efforts to bring supporting products to market, held their iNNOVATION awards competition. Winners included products that enable wireless physical access control, converge physical and logical access, identify a vehicle and its driver at long range, and facilitate easy creation of contactless applications and products.
AVISIAN Publishing’s editorial team served as judges for the awards. To evaluate the twenty entrants and determine the awardees, a scoring system was developed by the judges based upon the following measures of ‘innovation:’
“The field of products was exceptional making our selection process challenging,” said Chris Corum, Executive Editor of AVISIAN Publishing and one of the award judges. “The ultimate winner, the AIR ID Converter from RF IDeas, scored high in all categories and really defines innovation.”
“As an OEM module, it facilitates the launch of new iCLASS-enabled products … In fact, a number of the other products in the competition rely on the AIR ID Converter,” he added. “Plus, it enables integrators and end issuers to rapidly build custom applications that capitalize on the HID credential for use beyond physical security into logical access and multi-application environments.”
The iNNOVATION 2006 event provided a great showcase for emerging contactless solutions. Said Debra Spitler, HID Global’s executive vice president of HID Connect, “it is rewarding to see partners develop solutions to support end-user requests … that leverage the use of existing HID credentials to solve business problems.”
 First Place:
First Place:
AIR ID Playback Converter
RF IDeas, Inc.
Accepting the award: Greg Gliniecki, Vice President
RF IDeas AIR ID Playback Converter permits users of HID’s iCLASS read/write readers, such as the RW400, to quickly deliver solutions. It is currently in use in truck scale, manufacturing and kiosk applications interfacing to backend systems. According to Mr. Gliniecki, “the converter completely removes all software development tasks and allows OEMs and end users alike to quickly bring out full solutions for nearly all applications in as little as an hour.”
The AIR ID line opens iCLASS to any operating system, including Windows, Unix, Linux, Macintosh as well as embedded applications, enabling support for existing applications under these environments. The converter expands the RF Ideas line beyond the PC, to non-desktop and outdoor environments. The AIR ID Playback converter is available today in USB or RS-232. The USB converter outputs as keystrokes while the RS-232 output ASCII characters.
Second Place:
Nedap Transition Booster
NEDAP AVI
Accepting the award: Gorm Tuxen, Business Development the Americas
Nedap’s AVI (Automatic Vehicle Identification) Boosters are in-vehicle reader transmitters, that allows a driver to use a standard building access credential such as an HID prox, iCLASS, ISO 15693, and ISO 14443 card for vehicle access. The card’s output is ‘boosted’ distances up to 33 feet and can be read at speeds in excess of 125 Mph. The Combi Booster adds an imbedded vehicle ID to the personal credential ID, enabling identification of both the vehicle and its driver. Visit www.tuxen.us/nedapavi for more information on driver based vehicle access.
Third Place:
Sig-Tec Convergence Solutions
Sig-Tec
Accepting the award: John McGuire, Regional Director
Sig-Tec’s Convergence software enables both logical and physical security using iCLASS cards, proximity cards, biometrics, and tokens. Added to the company’s prior solutions that addressed logical access security, print security and remote desktop access security is a physical security based on HID’s Vertex controllers and iCLASS credentials, Omnikey readers, and Sargent door locks. According to Mr. McGuire, the solution is extremely scalable and cost effective enabling convergence solutions within the reach of small and mid sized organizations.
Honorable Mention:
Wireless Access Management Solution (WAMS)
OSI Security Devices
Accepting the award: Derek Trimble, President
The WAMS solution provided end-to-end (door to host) wireless communications using OSI’s Omnilock battery powered reader/lock units and HID credentials. Combining battery operated lock mechanisms with the installation and communication ease of wireless cuts the costs and disruption of retrofitting access control environments. The user gets the functionality of a software-based system at a lower cost with little or no interruption to their business. With no controllers required, no modifications to doors, and no electrical needs at the door, the system is easily added to and can be removed and re-installed in another location.
 Understanding who pays, who gets paid, and how to make sure your cardholders win
Understanding who pays, who gets paid, and how to make sure your cardholders win
ATMs are a convenient and quick source for cash. But they also can be expensive if you’re using an ATM that is not owned by your bank. For a college student on a budget ATM fees, even at $1 or $2 a pop, can add up. Understanding the various types of ATM fees, including foreign fees and surcharges, can help campus administrators select the best bank partner to serve their students via the campus card program.
 ATM fees explained …
ATM fees explained …
ATM fees are usually levied when you attempt to use your bankcard at an ATM machine owned by another bank. Typically, your own bank will charge you a fee, called a “foreign fee,” to cover the costs they are charged directly when you use an ATM owned by another financial institution. Additionally, the bank that owns the machine may charge a fee, known as a “surcharge fee,” for using its ATM. In essence, when you don’t choose the ATM carefully you may be paying two fees for a single transaction.
The first thing to consider are the parties involved in an ATM transaction: the cardholder’s bank, the ATM network, and the ATM owner. Each of these parties incurs costs when a cardholder uses an ATM. It is only logical that each of these parties levies fees to cover their costs and make money.
When a cardholder uses an ATM that is owned by their bank, the transaction is called an “on us” transaction. No other bank or ATM owner is involved in the transaction so only the ATM network and the cardholder’s bank are entitled to fees.
When a cardholder uses an ATM that is owned by another bank or private ATM owner, the transaction is called a “foreign” transaction. In such a case, all three parties incur costs and thus levy fees. The ATM owner has the costs associated with deploying and maintaining the machine, the network uses its infrastructure to route the transaction, and the cardholder’s bank must approve and moderate it.
With “on us” transactions, the costs are most often absorbed by the cardholder’s bank as a service to their customer. Foreign transactions, however, typically result in two separate fees to the cardholder.
First, a fee called a surcharge is levied at the time of the transaction. This fee is detailed on-screen at the ATM, usually taking a form such as, “the owner of this ATM charges a $1.50 fee for use of the device.” The cardholder is asked to accept or decline the fee and, subsequently, the transaction. This fee is shared between the ATM owner and the network.
A foreign transaction also commonly results in a second fee assessed by the cardholder’s bank. This fee appears in the monthly statement and is designed to cover the expenses that the cardholder’s bank incurs during the transaction. This fee is set by the cardholder’s bank though a portion of it is shared with the ATM owner.
For years there have been consumer complaints that ATM owners were, in essence, double-dipping by surcharging and sharing in the foreign fee collected by the cardholder’s bank. There were pushes to ban surcharging brought from many levels (in fact, surcharging was not allowed in the early days of ATMs).
The reality, however, is that this it is the surcharge that has enabled ATM deployment to proceed to the extent it has occurred. Without surcharges, it would be difficult to make money deploying and operating the devices. The surcharge has changed this and created a major business in ATM operation. This has led to significant convenience–with an ATM on almost every corner. Consumers can avoid fees by using devices deployed by their bank, but they can also benefit from the convenience of ready access if they are willing to pay the additional fees.
Evaluating ATM networks for your campus card program
“Students love to use ATM machines, but they hate to pay fees,” says Whitney Bright, vice president and general manager for U.S. Bank Campus Banking. She suggests that ATM availability and fee structures should be one of the issues a college examines when evaluating a potential bank partner. Not only should the college ask the bank if it will provide ATM machines on campus (that should be a given), but what kind of network does it have beyond the campus.
Will students be able to access ATM machines–without paying a fee–when they go home for the summer? “As you’re evaluating a potential banking partner, you should look for one with a large ATM network,” Ms. Bright advises colleges.
“When we partner with a school like Northwestern University, with students who come from all over the country, they want to be able to use their U.S. Bank account tied to their WildCard when they go back home, thus avoiding fees,” she said.
But, it’s not always that simple. The on-campus bank may not have branches or ATMs in all communities. That leaves the student with limited options: Open two accounts, one back home and one on campus, or sign up with a bank that has branches in both locations.
Or, choose door No. 3. Even though your on-campus bank may not have a branch back in your hometown, it could be a member of a network that specializes in offering surcharge-free ATMs.
Surcharge-free ATM networks
U.S. Bank chose that option last year when it purchased Genpass, owner of the MoneyPass Network (www.moneypass.com), a system of more than 7,000 surcharge-free ATMs. In addition, the student checking account at U.S. Bank waives the first four foreign ATM transactions per month giving students and option to use MoneyPass ATMs with zero fees across the country.
“This is a big advantage for students who want to use their account with no fees anywhere they travel in the country,” said Ms. Bright.
The bank’s membership in the Moneypass network adds another 7,000 ATMs that U.S. Bank customers can access, even if there isn’t a U.S. Bank in their hometown. The bank also operates some 5,000 ATMs that its customers can already use fee-free.
MoneyPass isn’t the only surcharge-free network, or even the largest. That honor goes to Allpoint (www.allpointnetwork.com), which offers some 32,000 ATMs. Another is NetBank (www.netbank.com/bankingcardsatm_free.htm) which has the nation’s second largest bank-operated ATM network.
Alliance One (www.atmallianceone.org/AllianceOne) is a nationwide group of select-surcharge ATMs in 37 states, Puerto Rico and the District of Columbia. Alliance One is a nationwide cooperative group of credit unions, community banks and thrifts that have joined forces to let their cardholders access each others’ ATMs without having to pay ATM surcharge fees.
Student-friendly ATM fees should be a part of a sound bank partnership
“If you’re considering a banking partnership with your campus ID, look at the many different things that can make a bank partnership successful with the university long term,” Ms. Bright advises colleges. A surcharge-free ATM network can go a long way towards keeping your students happy, while saving them money.
 Sweden’s Göteborg University deploys a visual challenge and response solution from Entrust
Sweden’s Göteborg University deploys a visual challenge and response solution from Entrust
By Andy Williams, Contributing Editor
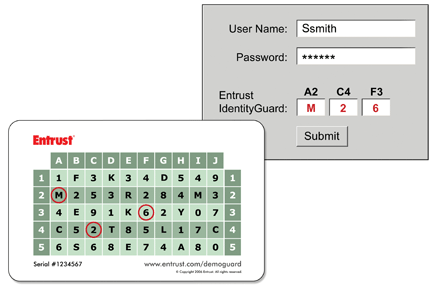
You log in with your password, then you’re met with another screen with the following: A3, F4, J5. No, you’re not playing Bingo. It’s part of an authentication system created by Dallas, Texas-based Entrust. To supply the correct answers to A3, F4 and J5, you need a grid supplied by the company. It’s a security solution that one Swedish university has chosen to protect its student records.
“Grid authentication is about an X-Y coordinate lookup system,” said Steve Neville, senior manager of ID products and solutions for Entrust, Inc. a secure digital identity provider. “It’s like reading a map and it’s about being able to respond to the random challenges of a coordinate on a grid.”
 To help prevent attacks on student data and protect the records of its 60,000 students and faculty while facilitating access for authorized parties, Göteborg University in Sweden recently implemented Entrust’s IdentityGuard. The campus, one of the largest in Scandinavia, joins a Tokyo college and “several others across Europe (that) are using it for their students and faculty also,” said Mr. Neville.
To help prevent attacks on student data and protect the records of its 60,000 students and faculty while facilitating access for authorized parties, Göteborg University in Sweden recently implemented Entrust’s IdentityGuard. The campus, one of the largest in Scandinavia, joins a Tokyo college and “several others across Europe (that) are using it for their students and faculty also,” said Mr. Neville.
A cost-conscious option for multi-factor authentication
The two-factor authentication system requires a password, plus the grid that’s often printed on the back of a student’s or faculty member’s identification card, said Mr. Neville. It’s a standard student card that’s usable not only for identification but for other things, like accessing foodservice.
“Some organizations provide more flexibility and allow their customers to print out the grids, or store them and send them, via SMS, to their phone,” he added.
 Either way, the grid is useless without the password and the password useless without the grid. The grid is the ‘something you have’ and the password is the ‘something you know’ in the multi-factor authentication scenario.
Either way, the grid is useless without the password and the password useless without the grid. The grid is the ‘something you have’ and the password is the ‘something you know’ in the multi-factor authentication scenario.
This kind of authentication “has been a bit more accepted in the rest of the world than North America,” he said. “North America has always lagged in deployment of second factor authentication. In Europe it’s been accepted and understood as a requirement for many years. I expect to see these things in North America take hold there soon.”
“We wanted an authentication solution that would provide strong security but also would be easy to use for our students and faculty and also be economical to manage,” said Sven-Elof Kristenson, IT manager at Göteborg University. “Because we can combine the Entrust IdentityGuard grid authentication capability with the identity cards we already issue to our students and faculty at the beginning of the school term, it fit seamlessly into our existing system and will give us the ability to make even more services available online for everyone.”
The university also chose IdentityGuard because its grid authentication capability can be used to access records, file storage, reports, e-mail and calendar functions, said Mr. Neville. “It was a natural choice for stronger authentication. Ease of integration and usability also were factors that led to the decision to implement Entrust IdentityGuard.”
Adding ‘machine fingerprinting’ to the grid authentication
“ID Guard in and of itself is a platform for authentication,” said Mr. Neville. It comes in six different flavors–authentication options–ranging from the non-intrusive like machine fingerprinting and grid authentication to one-time password tokens, he added.
“One of the reasons Göteborg liked grid authentication is that it also delivers the flexibility to input other types of authentication. Inside our license model we don’t force them to track which authentication they’re using. They can choose which ones they want to use to protect student data,” said Mr. Neville.
A risk can be assigned to student data to determine the type of authentication needed, he added. “It can be a simple process, like this type of information requires the grid and machine authentication. For students, the grid is totally fine because they’re roaming around,” said Mr. Neville.
ID Guard is a “software server based product that can also provide strong authentication for remote access,” he added.
“What we’ve done is open platform. We support adding different authenticators. You can add machine fingerprinting, literally being able to capture parameters of an individual machine such as its IP address and its browser settings. If that person is coming in from a registered machine, on subsequent authentications it can transparently check.” If not, he’ll be prompted for more security, such as a password.
“It’s all about increasing the security of a machine without affecting the user,” said Mr. Neville.
“When they (Göteborg University officials) were looking at security solutions, they were very sensitive to cost and how much change would be required. They looked at ID Guard as a very attractive solution versus one that could only be deployed to faculty alone because of the cost. It was also something they found very unique and something they could trust.”
Are displays for smart cards finally more than just talk?
Marisa Torrieri, Contributing Editor
It’s your credit card … spiked with something extra … a thin, flexible display with a readout similar to that of a calculator. But you don’t just make transactions with this card. With this baby you make them two-factor style, fusing something you know (your card number), with something you definitely have in your possession (your card).
Why would a cardholder care?
Here’s one reason: in growing digital-transaction real-world scenario, where more and more purchases are made online, the party on the other end receives your card number and security code, but there’s no way of knowing that you actually are the one holding the card. No biggie … until some ID-stealing thief’s trying to purchase a dozen iPods online using your number.
Fortunately, this new kind of card is on the horizon, and will allow consumers to conduct secure transactions with two-factor authentication with ease. A growing number of companies are developing thin, password-generating card displays that can be incorporated into your trusty cards. Equipped with displays, that can now be mass-produced at rapid speed, these new powerful cards generate single, numeric pass codes that change at the push of a button, transaction to transaction. In the future, people will be able to
view things such as recent bank transactions and credit card balances – on the cards themselves.
Because U.S. consumers and the financial institutions that serve them continue to resist technologies such as One-Time-Password tokens, that make consumers do more work to secure their transactions, display-equipped cards are generating a great deal of interest as an alternative for secure two-factor authentication.
In the next six months, a number of companies working with electronic displays, like Aveso Inc., SmartDisplayer, and InCard Technologies, are hoping to see their slender, powerful, high-tech wares bear fruit.
Financial applications are, arguably, the hottest and most promising markets for display technology cards, thanks to nearly one-year-old Federal Financial Institutions Examination Council (FFIEC) guidelines, recommending that institutions to bear the burden of incorporating two-factor authentication methodologies into their offerings to enhance security.
“This is another hardware or token format,” says Emily de Rotstein, executive vice president of marketing for Aveso Inc., a company that develops printed electronic displays. “If you’re a bank in America, you can brand the card, personalize the card, and add OTP functionality to the card itself. It’s the logical next step in the evolution of a payment card for secure online authentication.”
 According to Ms. de Rotstein, technology such as Aveso’s allows for easy integration of electronic displays into high-volume printed products such as credit cards and packaging labels. Because displays are produced using existing print-manufacturing techniques, display devices can be scaled cost-effectively in the hundreds of millions of units, volumes required to support a global industry standard for the electronic display card.
According to Ms. de Rotstein, technology such as Aveso’s allows for easy integration of electronic displays into high-volume printed products such as credit cards and packaging labels. Because displays are produced using existing print-manufacturing techniques, display devices can be scaled cost-effectively in the hundreds of millions of units, volumes required to support a global industry standard for the electronic display card.
How the technology works, why it makes transactions better
Sure, the form factor – a slender, powered card that give you a one-time-password, and may even be able to display credit card balances – is a sexy proposition. Especially in light of the FFIEC guidelines. But what about the technology?
To get an idea of how a thin electronic display works, one must first understand that it is just one of three critical components of a display card: the other two are the battery (the power source, which allows for a number to be generated), and the microprocessor (the chip that runs algorithmic applications to generate numbers).
Display technology allows for a one time passcode to be generated and show up, on a card’s surface, within seconds. So a person holding the card possesses two-factor authentication – something they know (secret password), and something they have (the card itself). The combination lessens the likelihood of identity theft.
And that’s just for starters.
The display card will potentially be able to display all sorts of information to its users; numeric, electronic displays give numeric information, for example.
“Thin and flexible electronic displays enable new applications that have not been possible displays that have not been possible in the past due to the limitations of the traditional, glass-based displays,” says Ms. de Rotstein, referring to glass-based, liquid crystal displays found in such applications as watches and phones. “Traditional displays are often too thick or too fragile for integration into the standard credit card. By overcoming these hurdles, plastic, flexible displays will transform the payment card and deliver benefits to consumers and card issuers alike.”
It’s those applications Innovative Card Technologies (InCard) is banking on in a series of pilots set to begin in the fourth quarter of 2006, says CEO/Founder Alan Finkelstein.
“The world is becoming aware that a random generator is the fastest, most cost effective way to get secure technology to the mass market,” says Mr. Finkelstein.
InCard is the exclusive provider of a flexible display technology called SmartDisplayer, developed by the Taiwanese company of the same name, as it relates to displays placed in a card form factor.
InCard Technologies recently created its DisplayCard with OTP and it plans to pilot the card later this summer. The card, via an embedded chip and an display, generates an OTP at the push of a button. Then, the card is authenticated by a secure server to confirm that the genuine cardholder is the one making the transaction.
So, by the time cold snow has replaced this slip-and-slide summer, will interest in these cards generate a new kind of heat? InCard, for one, is crossing its fingers. “When we started to look into this three or four years ago, we met with everybody who was trying to develop technology and components like these,” says Mr. Finkelstein. “From the time they showed us a display that was working, it still took three years of R&D and many millions of dollars.”
Still, the bottom line comes down to consumer behavior, the perceived
necessity of two-factor security, and, according to Mr. Finkelstein, the question: “Do you want to carry two or three of those tokens or would you rather put a card (with a flexible display) in your wallet?”
 For more than 20 years, Assistance League® of Las Vegas has promoted volunteerism, dedicated to meeting the needs of its community. Part of the National Assistance League®, the organization’s 292 volunteer members logged over 32,000 volunteer hours last year in support of philanthropic projects.
For more than 20 years, Assistance League® of Las Vegas has promoted volunteerism, dedicated to meeting the needs of its community. Part of the National Assistance League®, the organization’s 292 volunteer members logged over 32,000 volunteer hours last year in support of philanthropic projects.
Access Control Needed
Access control, in support of the large volunteer staff and on-site retail facilities, is a constant and vital requirement for the organization. The League’s headquarters, the Donald W. Reynolds Chapter Facility, had existed since its completion in October 1998 with traditional mechanical locks.
After experiencing several break-ins due to faulty locks at the facility, League management was desperate for a new access control solution. The organization went to a group organized by the Associated Locksmiths of America (ALOA) to research the cost of new locks for their facility. In conjunction with the ALOA Convention in Las Vegas, a cooperative organization comprising representatives from three concerns (Associated Locksmiths of America, OSI Security Devices and ACE Locksmiths) was able to respond by donating a state-of-the-art access control solution for the Assistance League.
State-of-the-Art Keyless Solution
With a goal of providing greater security and access control to the Assistance League facility, 13 doors were installed with the high-tech Omnilock Wireless Access Management System. Donated by OSI Security Devices, Inc., the installed system replaced the League’s old lock system. The system uses HID Global’s proximity technology and incorporates programmed access cards, donated by HID Global. Additionally, several Von Duprin exit devices and associated installation time were donated by Security Lock Distributors and ACE Locksmiths of Las Vegas, providing additional resources for the installation. Hardware for the new system is valued at $15,000 - $18,000, with twice that amount given by locksmith installers, in labor and installation costs.
The Assistance League facility is one of the nation’s first non-government commercial installations with Omnilock door locks. The lock system includes a battery-operated mechanism that can be used with HID proximity cards, a touch pad system, or both together, customized for each volunteer for heightened access control. In addition, a log of entrants into the building, forced entries, outages and battery power is recorded by the software component of the system, providing increased access control intelligence to the League’s management. The entire system enables end users to log on to the system and run their access control application remotely.
The installers, many with their first chance to work with the keyless, wireless, battery-operated Omnilock system, gained valuable training and experience with the new system while providing a valuable service to this community center.
“With a very worthy cause, and an opportunity to advance the training of ALOA members, it was not difficult step-up to the plate and donate the WAMS system for this project,” said Ron Siess, OSI Security Devices Vice President of Business Development. “It was a very instructive day and The Assistance League of Las Vegas was very grateful to all who contributed to the project.”
“This looked like a perfect opportunity to launch off a new access control system,” said Jerry Newton, Ace Locksmiths’ CEO. “I like what they do and it’s great to see somebody trying to do some good.”
Touching Lives through Cooperation
The ALOA-sponsored group helped to provide valuable assistance and an innovative security approach to this critical community organization. League funds that would have been spent on an access control system will now be reallocated to assist initiatives like Operation School Bell, providing clothing and school supplies to underprivileged 5- to 15-year-olds, increasing their incentive for attendance, academic performance and self-esteem.
“To us, this is such a boon because the money we need is for the children,” Assistance League’s Margy Purdue-Johnson said.
About OSI Security Devices
OSI Security Devices, shortly after it’s founding in 1986, introduced one of the world’s first battery-operated stand-alone electro-mechanical locks. Built to stringent military and industrial specifications, Omnilocks have been successful in meeting the demands of government, university and industrial customers throughout the United States. Stand-alone reader/locks programmed by PDAs have solved difficult access control challenges in some of the toughest environments imaginable. OSI has now introduced WAMS, which stands for Wireless Access Management Solution. This system allows easy upgrades for their stand-alone systems and provides a full featured, software based system, which is totally wireless end to end. OSI is headquartered in Chula Vista, California. To learn more, please visit www.omnilock.com.
About HID Global
HID Global is a leading manufacturer in the access control industry, serving customers worldwide with proximity and contactless smart card technologies; central station managed access controllers; secure and custom card solutions; digital identity and photo card management software solutions; secure card issuance solutions; and RFID electromechanical cylinders. Headquartered in Irvine, California, HID Global operates international offices that support more than 100 countries and is an ASSA ABLOY Group company. To learn more, please visit www.hidcorp.com.
 By Andy Williams, Contributing Editor
By Andy Williams, Contributing Editor
A group of grad students at the University of California, San Diego (UCSD) are in the process of creating what one of the students calls the “most over-designed soda machine in the world.”
Right now, the machine has attached to it a barcode scanner, a fingerprint reader, and a web cam for facial recognition. Want a Coke? Stick your thumb on the reader so the machine recognizes you as having an account, take out the drink, then walk way, never having had to reach into your pocket for change.
The project, called SodaVision (sodavision.com), is the brainchild of UCSD engineering associate professor Stefan Savage.
“I came up with the idea in June, 2005, but we didn’t get the soda machine until later that year. I had some discretionary money, so I bought a generic machine,” he said. “The biggest problem was putting through a purchase order for a ‘biometric soda machine.’ I got a few weird looks. I never actually gave the project the name. That came from the students.”
 He said the computer science department at UCSD has had a soda and snack cooperative, nicknamed Chez Bob by the students, for some 20 years. “You would put in 50 cents and take out a coke. About 10 years ago, someone came up with the idea that you could log into a computer, list the amount of money you’re depositing into the (Chez Bob) account; then when you buy a coke, log that in against your account,” said Dr. Savage. “I thought, ‘Here we are a leading computer science program, we should have something better.’ So, I offered it as a project for the grad students.”
He said the computer science department at UCSD has had a soda and snack cooperative, nicknamed Chez Bob by the students, for some 20 years. “You would put in 50 cents and take out a coke. About 10 years ago, someone came up with the idea that you could log into a computer, list the amount of money you’re depositing into the (Chez Bob) account; then when you buy a coke, log that in against your account,” said Dr. Savage. “I thought, ‘Here we are a leading computer science program, we should have something better.’ So, I offered it as a project for the grad students.”
What SodaVision ended up becoming–and it’s still a work in progress–is what second year computer science grad student Tom Duerig calls “the most over-designed soda machine in the world.”
“I wanted it to be incredibly easy to use,” said Dr. Savage. “I bought the soda machine and a touch screen and the fingerprint reader, a Fujitsu MBF 200. We looked for a fingerprint reader that would work with our software and with Linux. Now they (about 10 students) have actually torn (the fingerprint reader) apart and rewired it to work with the machine.”
The students built the interface. “I had one guy design a touchscreen that looks like the one used in Star Trek. Somewhere along the way they added a camera and another group added a 2D laser barcode scanner,” said Dr. Savage.
The camera, a web cam, is for facial recognition, the next big step in the technology-heavy machine. “The students even wrote the software to recognize the images,” he added.
“Our goal is to have the soda machine simply recognize who is standing in front of it when a soda is vended or money is inserted to charge or deposit into the appropriate account. And thus was born SodaVision,” wrote Mr. Duerig in a paper explaining the project.
As he further pointed out in the same paper: The camera “is trained on users faces, which are added to the repository. Recognition requires detecting a face, morphing the face, running preprocessing on the face, looking up the face in the repository, running an election over many frames, and finally logging in the user with the most votes in the election.”
The brain inside SodaVision is a small computer designed for cars. It is stored inside the soda machine and is equipped with an Intel Celeron 2GHz processor with 512MB of RAM. The computer fit the students’ needs in that “it was very small, slow, quiet, and didn’t produce a lot of heat,” explained the 23-year-old Mr. Duerig. “We briefly considered putting a quad CPU 1U server in there as that would have fit, but we decided against it for heat reasons.”
“The students have been entirely cooperative in this project. It has created a tremendous esprit de corps, a lot of energy and excitement,” said Dr. Savage.
The machine is available to grad students, faculty and staff in a locked room accessible via a card reader on the door.
While the team of grad students concentrate on increasing the accuracy of the facial recognition software, Dr. Savage still utilizes just the fingerprint reader. “I use it every day, because I’m used to using the reader.”
“The only way to purchase soda is when you’re logged in (currently via the fingerprint reader). You can also deposit money into your account (through a slot attached to the machine),” said Mr. Duerig. When a user vends a soda, his/her account is automatically debited. A candy bar or other snack item is scanned with the barcode reader and charged against the user’s account.
Right now, the facial recognition part of SodaVision is carrying an 80% accuracy rate. “We’re shooting for 95% accuracy.” Eventually, the plan is for “dual recognition,” added Mr. Duerig. You sign in with your thumbprint, and then go for facial recognition. But until we hit the magic 95% accuracy, it isn’t integrated with the payment/purchase system,” he added. “I suspect we’ll hit that mark at the end of this summer for the unveiling of the project.”
While the camera is there primarily for humans, it can be used for other things as well. For example, said Mr. Duerig, “We’re looking at ‘facial’ recognition for bananas because they don’t have barcodes.”
During the summer, SodaVision sees 20 to 50 users a day, but during the fall usage picks up. “In the fall I get about 10 emails for every five minutes the system is acting weird,” said Mr. Duerig.
 Even in a post 9-11 world, college campuses remain fairly open. Anyone can enter the campus itself with barely a nod from security. Corporations are a different matter and many have hardened building access in recent years. So, too, have K-12 schools. But with more options and lower costs, is it now time for colleges to take another look at better controlling visitors to their campuses? Supporters of visitor management solutions think so.
Even in a post 9-11 world, college campuses remain fairly open. Anyone can enter the campus itself with barely a nod from security. Corporations are a different matter and many have hardened building access in recent years. So, too, have K-12 schools. But with more options and lower costs, is it now time for colleges to take another look at better controlling visitors to their campuses? Supporters of visitor management solutions think so.
“Colleges are watching ingress and egress better than they used to do,” said Steve Blake, director of secure systems for Fargo Electronics, whose printer/encoders are used in visitor ID management systems. “But adoption has been better for visitor management in K-12 than in post secondary schools.”
Had some kind of visitor management program been in effect at the University of Cape Town in South Africa, a university professor might have avoided being beaten up by people who easily gained access to the building housing the professor’s office, as recently reported by a Cape Town online news service.
It’s one of the tradeoffs for having an open campus, a quality in which most colleges take pride. But are those days numbered?
 “(People are) implementing both unattended and attended visitor management systems,” explains Mr. Blake. “However, if you’re concerned about security, there is no reality to using an unattended system. I’ve been to several schools where you print out your own badge. It’s based on the honor system and it will work only for those who are honorable.”
“(People are) implementing both unattended and attended visitor management systems,” explains Mr. Blake. “However, if you’re concerned about security, there is no reality to using an unattended system. I’ve been to several schools where you print out your own badge. It’s based on the honor system and it will work only for those who are honorable.”
Visitor management systems were in use even before 9-11. “They’ve been available for about seven years,” said Mr. Blake. “But there was a low level of adoption until the last couple of years. What has changed is that prices have come down to where they’re more affordable. New technology also makes it much easier to go through the registration and badging process.”
But it took “9-11 for visitor management (and other security systems) to skyrocket,” added Mr. Blake.
Some of the more popular visitor management programs are the ones that allow a visitor’s driver license to be swiped or scanned, thus providing a visitor’s critical information along with his picture. Then a temporary badge can be produced, usually in less than a minute, complete with photo.
“Driver license scanners can be tied to the software. A school clerk will take your driver license, run it through a scanner and be able to print a card with a Fargo printer in color or black and white, within 30 seconds,” said Mr. Blake. “This is what’s really driving the growth in visitor management. If anything happens, the school has the front and back of the visitor’s driver license.”
Despite the ease of creating visitor IDs, it could still be difficult for colleges to implement. “The issue is that with colleges, they tend to be an open environment with a lot of public access,” said Mr. Blake. “If you’re going to have attended locations for visitors you might have multiple points of issuance. Some (colleges) do use ID cards for visitors, but there hasn’t been a high level of adoption here.”
To date, the real adoption of visitor security has been in the corporate arena, Mr. Blake added.
Selecting a visitor management system from the host of options
Do a Google search on “visitor ID badge management” and nine different products show up on the first page alone.
Some of the bigger providers of visitor ID management software include Avery and Brady ID, plus “there are a lot of homegrown ones out there as well,” said Mr. Blake. Most work with ID card printers, but Avery’s for example also prints on paper labels.
Another aspect of visitor badge management is whether it will be standalone (located on a single computer) or tied to the network. Standalone architecture is obviously easier since all data resides on the PC at the front desk. But regardless of the system chosen, says Mr. Blake, implementation is simple. “You can be up and running in 30 minutes.”
Visitor management systems don’t require top-of-the-line printers to function adequately. “Our entry level printers tend to be the printer of choice for visitor management,” he said. “They contain just the features that are necessary. A visitor management solution typically doesn’t require high volume card production.”
Another consideration is how easy the visitor ID badge printer is to operate and maintain. “(Operators) need to be able to change ribbons and load the cards easily, so they can spend their time with people interaction, not printer interaction,” said Mr. Blake. “With our Persona C30 printer, for example, you can just pop the ribbon and cleaning cartridges in, unlike some printers where you have to deal with rolls of ribbons or cleaning rollers. Ease of use is extremely important. Operators can’t be afraid of what they’re about to use.”
Visitor management software has also evolved, said Mr. Blake. “They’ve migrated to include modules that are not only people-related, but will handle packages as well. For example, if UPS or FedEx delivers packages to the front desk, the software allows the packages to be logged in … right at the front door to create a history, an audit trail, of that package internally.”
With lower prices, more products from which to choose, and ease of use, “maybe it’s time for colleges to take another look at this,” said Mr. Blake. “There has been great adoption (and successes) elsewhere. This could be the time for colleges to examine how visitor ID management can benefit them.”

