Transact+CBORD has launched CS Gold 9, the latest version of its long-standing campus ID and transaction system used at more than 250 institutions. Designed to streamline administration and boost functionality, the new release integrates artificial intelligence, improves the user interface, and adds customer-driven enhancements.
Steve Swingler, Senior Director of Software Development, says the AI-powered Ask CS Gold feature has generated strong enthusiasm.
Western Connecticut, University of Tennessee Knoxville, and Vanderbilt were the first three schools to go live. It's released. We're quoting to customers. We're ready to do more installs.
“Admins can ask a natural language question through the web interface, and the AI figures out what they're asking for, queries the database, and gives them back an English language response,” he explains.
Early adopters—including Western Connecticut, the University of Tennessee Knoxville, and Vanderbilt—have reported smooth, simple implementations.
Read Winkelman, Vice President and Campus ID Business Leader, emphasizes that client input guided many of the upgrades. “The ten features that got the most votes in our customer ideas portal were included in this release,” he notes. CBORD even credits the contributing campuses by name in the release notes.
The redesign includes new setup wizards, time-saving templates, and a cleaner interface across 16 of the most-used screens—changes aimed at making the system easier to navigate for both experienced and backup administrators.
Beyond administrative convenience, CS Gold 9’s AI capabilities help campuses analyze student engagement.
“Ask a question and say, ‘give me a list of students who haven't used their meal plan more than once a day in the last week,’ and maybe that’s an indicator that they're disengaged,” says Winkelman. “At least a way to start mining that data and look for students who might need some extra connection.”
Feedback from pilot schools has been overwhelmingly positive, with early users calling the upgrade “seamless” and “a win” for simplicity and usability.
To watch the full interview, click the image at the top of this page.
TRANSCRIPT
Hello there, and welcome to this episode of Campus ID News Chats. I'm Chris Corum, your host and publisher of Campus ID News.
Transact+CBORD just released a new version of the long-standing CS Gold platform. We're going to talk today about the new version that was just released with CS Gold 9 with two of the company's leaders.
Welcome Read Winkelman, Vice President and Campus ID Business Leader, and Steve Swingler, Senior Director of Software Development. A little background on the two of them, it’s been 20-plus years with CBORD for both, 30 for Read, and if you add in Steve's time at Diebold, which became a part of CBORD, he's at 30 years too. Both worked on a campus as well.
Chris: So how about a little history of CS Gold before we talk about the new version, when it came out, how many campuses use it, that kind of thing.
Steve: We came out with the first version of CS Gold back in that time that you referred to when we were at Diebold prior to coming over to CBORD. I think that was 1998, and it's grown to over 250 campuses.
It tends to succeed with our larger campuses where the needs are complex, campuses that are doing some very large access control, but we've got a loyal group of customers that give us great feedback, great ideas, and we'll talk in a little bit about some of that feedback that we made part of Gold 9.
Chris: Gold 9, what's new in this version? What was the goal with releasing it? And what did you learn from clients that went into it?
Steve: The one that we get the most comments, questions, and excitement about, I think, is Ask CS Gold. It's an AI chat interface where the admins can ask a natural language question through the web interface of the existing CS Gold web interface, and they ask a question that's on their mind, and the AI figures out what they're asking for, where that might exist in the database, it queries the database, gets the results, and gives them back an English language, natural language response, and the feedback on that has been fantastic.
We've also done some work based on our admins' feedback to save them time in some of the tasks that have been historically more time-consuming, things like building out a meal plan. We've created a new wizard style that gives them some templates from which they can start, so there's some standard templates. There's also the ability to copy an existing meal plan and then tweak that, so some time savers there, some other wizards for the admins, some export utilities.
But I'm real proud of the work the team did to improve the user interface on more than 16 of our most used screens. There's a new look; there's a new cleaner design to it that we're proud of.
Read: I think one of the biggest things, you kind of hit on it, but we have some of the top requested features from customers that they've submitted ideas to us. We have an ideas portal that they can submit ideas in.
The 10 that got the most votes were included in this, and one of the things that I think was pretty is when a new feature is documented in the release notes, the school that submitted that feature as an idea is getting credit right in the release notes. It's not necessarily the person because people move around, but that school is getting credit.
I think that the things Steve talked about in terms of some of the wizards and the ease of use of the user interface, those are nice things, and you think about, well, that's great.
It makes it easier to use, but that's really by design because if you think about the Campus ID industry, we have a lot of customers who frankly are starting to near retirement age, and even those that aren't are looking to be able to take vacations or have sick time. They have to bring in other people who are doing things with the system and doing some system administration, but they don't do it every day, so the easier we can make the system to operate, the easier it is to have somebody cover and back up a regular system administrator, so that was really part of what we were trying to get after with Gold 9 too.
Chris: One question on the AI thing that you mentioned. Can you give a specific example or two of what someone would ask. When you first said it, I was thinking, you know, what's the weather going to be like today in Tallahassee or something, obviously that's not it, but so what would be a query or something that could be really helpful for a user?
Steve: So you know, one simple example I used just to pick on my boss was I'll ask and show people when was the last time that he went into the office and at what time did he arrive, and you know, make fun of him if he arrived late, but that's just for fun.
You know, you can think of some really complicated questions, and it figures out the answers, so I could ask which locations are doing more than 10% more dollar transactions or number of transactions than they were a month ago, right?
Where am I trending to have the business increase or the same thing with decreases?
You can ask questions to identify students whose activity has declined over a period of time. I can say over a semester, over a month, over a week, and it figures out the complexities of the query, and these are things that we don't naturally have reports in the system to do, but someone on campus will reach out to the card office and say, hey, can you tell me this?
Rather than it being days or weeks long project to figure out how to get a report, they can go type the question and they're getting some remarkably good results.
We had a live demo at a NACCU Near You event in Knoxville. UT Knoxville is one of our beta customers, and now they're live, it's fully released, but they were confident enough in the solution to put it up on the screen live in front of this group of people and type in questions and see it generate the answers, so it's working well for people.
Read: I was just going to say, I think, you know, Steve's point about decline in transaction volume, one of the biggest things that campuses talk about these days is student success and student engagement, and we have all the data in a campus ID system.
Being able to easily ask a question and say, give me a list of students who haven't used their meal plan more than once a day in the last week or some, you know, is that an indicator that they're disengaged?
Maybe, maybe not, but it's at least a way to start mining that data and look for students who might need some extra connection, extra attention.
The other thing that I think it can be really helpful with is I've had, I don't know how many different schools who talk about the fact that students don't always monitor their declining balance funds, and they don't spend it because they're going to the dining hall and they get to the end of the semester and there's all this money backed up that they want to spend.
It's a way to help identify how people are using the system and then proactively reach out to them, whether it's for a student engagement thing or just to make good use of the money. Because kids that eat and kids that sleep do better in school, right.
Chris: Well, you hit on one of my next questions when you said that that UT Knoxville is live. Is CS Gold 9 out of pilot and live at a number of institutions?
Read: Yeah, we, so we had three schools that, and Steve was doing the implementation, so our development team was doing them. Western Connecticut, University of Tennessee Knoxville, and Vanderbilt were the first three schools to go live. They all went live early summer. We wanted to wait till we got through the back-to-school season in a regular load in terms of transactions before considering it generally available, which it is now.
It's released. We're quoting to customers. We're ready to do more installs, but those implementations were very simple. In a couple of the cases, our primary contacts weren't even on campus when we were doing the installations because they didn't need to be.
And since back to school has started, no, no issues whatsoever. Systems have continued to operate really well.
I should also mention Western Connecticut was the first one to go live. UT Knoxville is a mobile credential customer using the, the Allegiant flavor of mobile credential and Vanderbilt is also mobile using the HID flavor and Vanderbilt has some biometrics tied in. We feel like we've really tested all the various use cases that we could have with those three customers.
Chris: You mentioned that it was an easy implementation, but for the next Gold customer that wants to go to version 9, what is the implementation process actually look like?
Steve: If they're familiar with past upgrade exercises, for example if they went from CS Gold 6 to CS Gold 7 or CS Gold 8, it's very similar. Depending on the size and complexity of their system, you know, the downtime will vary significantly. But one thing is there is not a major database version change in this one, so that actually saves some time in most cases. There's no database conversion required.
Chris: I assume since the two companies came together that Transact releases might have some ties to see previous CBORD clients or products and back and forth. Are there some new things in Gold that tie to some of the Transact products?
Read: Yeah, we're doing a couple of things. One is, as you might imagine, all of the devices around the perimeter of the core system – so point of sale, access control – we're looking to make those as consistent across all the products as possible. So, when a customer wants to move from gold to, to IDX, they're ready.
But we've got CS gold customers that are currently implemented with our cloud point of sale solution, which is a Transact point of sale solution that we've had for a while that includes mobile ordering.
We've also taken our CS Access portion of CS Gold and we're live with an integration to TSE, which is a Transact campus ID system, the predecessor of IDX that's live now as well.
So yeah, absolutely. We're looking to tie things together so that when a customer wants to move to IDX, they're ready because all of those tie ins are already set up.
We're not trying to push anybody to move, but we want them to move when they see the feature and the value that makes them want to move.
Chris: Any client feedback that stands out like from the early three, I'm sure it's all good, but is there something that makes you, that made you go, wow, this is, this is great to hear?
Read: Rebecca at Western Connecticut keeps sending us emails of feedback she's got from people that interact with the system that are just sort of giddy about how easy it is to use. She's called it a win. Knoxville the upgrade was simple. Vanderbilt called it a seamless transition. It’s hard to ask for anything better than that. I think people are happy with the functionality and getting value out of it.
Steve: Sometimes it's the little things. We added a real simple export button to the patron groups interface. That was requested somewhere along the way and we thought, okay, well, that's, that's not too hard to do.
Rebecca showed that to a group of RAs for the first time and they were just elated. Now, you can imagine there's some patron groups associated with residents in a particular building and to be able to just download that list and use it however they want to use it was an exciting new feature for them.
I never imagined that that would excite anyone.
Chris: If somebody wants to learn more about CS Gold 9 or an existing customer wants to talk about upgrades, where do they reach out?
Read: Best process is to talk to their account executive. If they don't know who that is, my email address is CRW at CBORD.com. I'm happy to field anything. But if contact your AE, you'll get probably a faster response and a little more detailed as well.
Chris: Read, Steve, thanks so much for joining us and filling us in on the latest and greatest with the new version and to all those folks listening or watching or whatever you want to call it.
As always, I appreciate you being here and if you have any suggestions for a future episode of Campus ID News chats, shoot me a note at chris at campusidnews.com.
Modern identity cards and credentials rely on encryption for security. It is what separates a smart card, high-frequency contactless card, or mobile credential from older insecure technology such as low-frequency proximity cards, magstripes, and barcodes.
But what is encryption and how does it work in the credential world?
At the heart of this question is the encryption key, a string of data used to encode and decode information. In most card systems, there is a secret key that is shared between the card and reader enabling secure transactions to occur within the system.
Each concept is applicable to both cards and mobile credentials, and understanding them is key to making informed decisions for your campus card program.
“You can think of it as the variable in an equation – the equation stays the same, but the variable can change,” says David Stallsmith, ColorID’s Director of Product Management. “The credential and the readers must know the correct secret key to encrypt and decrypt the identity data.”
Only then will they communicate to open doors or conduct transactions. That's why encryption is the key to security.
Traditionally, most manufacturers have used their own standard encryption key in all their clients’ readers and cards.
Of late, however, there has been a push by some end users – including some campuses – for custom keys. Rather than using the manufacturer’s standard keys, these clients have requested dedicated keys unique to their system.
There are benefits and drawbacks to both approaches.
Standard or non-custom keys make ordering and provisioning of new cards and readers easier, faster, and sometimes cheaper. That is because the manufacturer does not need to customize them for the individual client.
But that positive also comes with a negative. Using the manufacturer’s standard key ties you to that manufacturer for cards and readers. The ability to order from multiple suppliers is reduced or even eliminated.
People that owned their custom keys during the pandemic had more options for card stock suppliers, but since the supply chain bounced back, that benefit has pretty much evaporated.
Another drawback of non-custom keys is that if the manufacturer’s standard key is compromised, it could impact all client sites. This could require replacement or reprogramming of all cards and readers.
Protection against a compromise at the manufacturer level is a benefit of custom keys. If it were to happen, end users with custom keys would not be impacted. It is important to remember, however, that custom keys are not immune to compromise. If not properly protected, they are arguably as vulnerable as non-custom keys.
“Depending on what type of card it is and how you manage that custom key, it can give you the ability to do other things,” says Todd Brooks, Vice President of Products and Technology at ColorID. “It can provide a bit of freedom as far as how you get your cards and how you encode the cards.”
For example, with custom keys the end user can program cards on their own rather than relying on the manufacturer do it. This allows them to buy cards from multiple suppliers.
“People that owned their custom keys during the pandemic had more options for card stock suppliers,” says Stallsmith. “This cut months off their lead time for card orders, but since the supply chain bounced back, that benefit has pretty much evaporated.”
Determining whether you want custom or non-custom keys is just the first decision. Next you need to decide if you’ll have your manufacturer hold those keys on your behalf or if you want to hold your keys within the institution.
At face value, holding your own keys – what some industry vendors call ‘owning your keys’ – seems like the obvious choice. Again, however, complexities arise.
Managing the keys yourself can be expensive and if not done properly can leave you vulnerable.
Most campuses wanting the benefits of custom keys have determined that they are not ready for the responsibility and liability of managing those keys on their own.
“When the manufacturer is holding the custom keys for you, there's security in that,” explains Brooks. “Managing the keys yourself can be very expensive and if not done properly can leave you vulnerable.”
Though far from the norm, he says, a small number of campuses have opted to manage their own keys, control their entire ecosystem, and decide how they're going to make their cards work on the different reader models they wish to use. It takes a more effort and more IT expertise, but it can be done.
Whether an institution uses custom keys or not, data needs to be encoded on the cards.
“Generally, cards are pre-programmed by a manufacturer like an HID or Allegion even if the end user has a custom key,” says Brooks. “In some cases, however, the campus will do it themselves either in the card printer using ID software or with a desktop device or USB reader.”
The idea of holding your own keys so you have total control of your system is attractive, but the practical application is limited.
To accomplish this, a Secure Access Module (SAM) that is purpose-built to securely stores keys is used.
“Whether it's a USB device or it's in the printer, it's basically the same SAM module,” says Brooks.
Very few campuses have taken on the responsibility to own or hold their own custom keys, so it is difficult to measure the value of doing so. Conceptually there are benefits, but they may just be conceptual at this point.
“The idea of holding your own keys so you have total control of your system is attractive, but the practical application is limited,” says Stallsmith.
He uses the example of a campus holding the custom keys for their DESfire cards. If the institution decides to change their access control reader manufacturer, it is true that holding keys could streamline the process. But there are only a few reader manufacturers to choose from, and ripping and replacing one access control reader for another is not an attractive or common decision.
“Sure, you can hold your own keys, but it's not like all of a sudden your world is going to dramatically change,” he says. “But if you have a very specific use, then then I guess it could be helpful.”
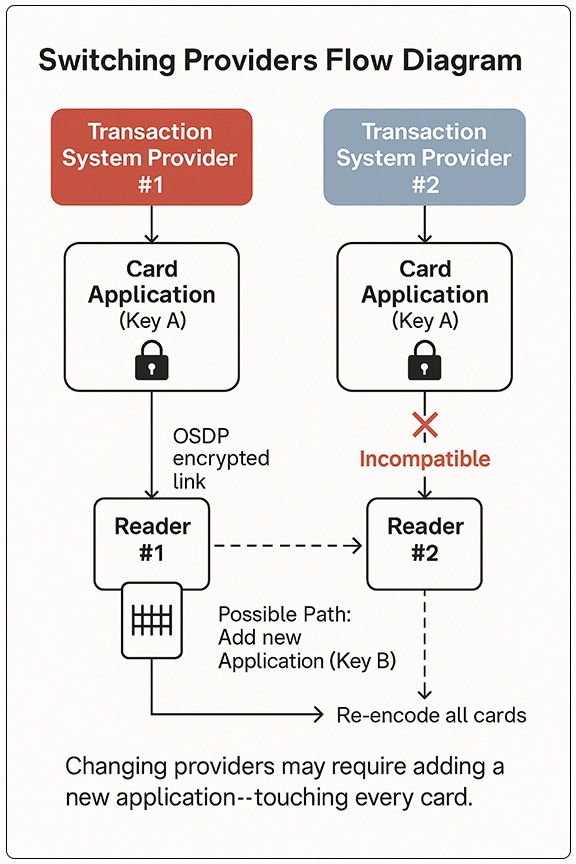 Encryption keys and transaction system providers
Encryption keys and transaction system providersIt is a common question: If I have custom keys or if I hold my own custom keys, does it make it easy to switch from one transaction system provider to another? The real question is more nuanced. You are really asking: Could I switch providers but continue to use my existing cards and readers?
In theory, you could because DESFire and other modern contactless credentials can store multiple applications on the same card. In most cases, however, the prior application will not work in the other transaction system provider’s readers and system.
“Just because you own your key doesn't mean that application you create using it will work on the different readers,” says Brooks. “It may require you to put two, three, or four different applications on the card itself to work with the reader infrastructure from the different transaction system providers.”
Think of it this way. You have an application on your card that is used in transaction system vendor #1’s platform. You replace vendor #1 for vendor #2. Just because you hold the encryption key and that key was used to create the first application does not mean it will work in vendor #2’s platform. The data, the format, and other elements would likely make them incompatible.
Of course, with modern multi-application cards, you could reprogram the cards to add a new application that supports vendor #2’s system, but that is easier said than done. It would require you to touch every existing card to add the new application. In a campus environment with thousands or tens of thousands of individual users, it just is not a realistic ask.
Stallsmith states it this way: “In a university setting, you don't get cards back.”
Though it garners a lot of discussion, it is rare for higher ed institutions to own or hold their own encryption keys. It can be costly, and it requires solid IT capability and commitment.
“I would say the key ownership discussion so far is largely theoretical,” says Stallsmith. “We've helped a number of customers get custom keys from manufacturers, which is often not easy because they haven't had to do it much.”
With OSDP you can centrally roll keys and not have to go from reader to reader to make changes. That makes the conversation around custom keys a lot more interesting.
This may change as access control readers move from using the older Wiegand protocol to the new OSDP protocol in greater numbers.
With the Wiegand protocol, the access control system can receive data like card numbers from the reader, but it cannot send information to the reader. The OSDP protocol, on the other hand, facilitates two-way communication between readers and the access control system. This enables the system to send new encryption keys to readers remotely without requiring a human to visit each reader for manual updates.
“With OSDP you can centrally roll keys and not have to go from reader to reader to make changes,” says Stallsmith. “At that point the conversation around custom keys is going to get a lot more interesting."
For most campuses, that's years away. For those with the means to do it now, however, there are more options.
The large card and reader manufacturers have been creating credentials with secure encryption keys for decades now.
While security breach and system compromise should always be top of mind, neither Stallsmith nor Brooks could point to a single instance of card or credential compromise at a systemwide encryption key level. This is true for both manufacturer’s standard keys and end user custom keys.
So, while real, to this point the threat is likely overblown.
Traditional large manufacturers are incredibly consistent at programming and delivering readers and cards. Another manufacturer may give you a custom key, but they may have a devil of time making cards on time.
This leads Stallsmith to point out that there's another side to the custom key discussion. He says that the traditional large manufacturers are incredibly consistent in their ability to program, update, and deliver readers and cards that work together.
“You just buy their readers, and you buy their cards, and everything works,” he says. “You can go with another manufacturer, they'll give you a custom key, but they may have a devil of time making cards on time.”
Perhaps the lesson is that it's not just the concept of the custom key that should determine what readers and cards a campus elects to use.
Like most decisions, there are many factors at play. In this series of articles, we addressed three of the most important – chips, formats, and encryption. Evaluating each of these concepts can help you make the best decisions for your campus.
In this episode of CampusIDNews Chats, Rob Stanford, the IT Manager for Facilities explains how Auburn University uses the DAX software solution from Detrios to simplify and automate critical campus processes.
Auburn relies on a complex network of systems, including Lenel OnGuard for access control, scheduling tools like Mazevo and Ad Astra, and StarRez for housing. In the past, these systems did not communicate effectively, forcing staff to manually update each one.
I could come up with a very high return on investment from a numbers standpoint, but just from a usability and efficiency standpoint, we've seen a huge return on investment.
As a single integration point, DAX connects the multiple scheduling platforms, the housing management system, and the access control system. Now, updates made in DAX automatically sync across all platforms, ensuring doors unlock when needed and access permissions are accurate.
“It started with a single building where we wanted students to access study rooms only if they’d reserved the space,” says Stanford. “From there, we’ve grown the system as more needs arose.”
The DAX solution has proven especially valuable during complex events, such as move-in day for student housing or unexpected weather closures. Instead of staff manually making adjustments in multiple systems, they can manage everything from one interface.
Stanford highlights how this automation has significantly reduced human error.
“You used to have to key something in one system, then go into another to apply access or pass it off to another department,” he explains. “When it’s all tied in, you’re making it more efficient and avoiding typos or miscommunication.”
This streamlined approach has allowed staff to focus on higher-priority work rather than repetitive administrative tasks. According to Stanford, the return on investment is clear—not just in cost savings but also in time, effort, and user satisfaction.
Beyond the technology itself, Stanford values the partnership with Detrios. When issues arise, he can reach out directly for fast, reliable support. This peace of mind is critical, particularly during high-pressure times like housing move-in.
For campuses looking to better connect their systems, Stanford offers a clear recommendation: “If you have a scheduling system and an access control system that don’t talk, you need DAX – or something like it.”
To watch the full interview, click the image at the top of this page.
TRANSCRIPT
At Auburn we have Lenel OnGuard as our access control system, and we have various different scheduling applications.
We have Mazevo, we have Ad Astra, we use Office 365, we have Calendars and Outlook, we also have a housing system, StarRez.
With all of those, we're trying to integrate. When you have certain events or things going on, you want those to be reflected in your access control system, make sure doors are unlocked, and people have the access they need.
We've been able to accomplish that using DAX and Detrios, it's been a really big hit.
It all started when we had some study rooms that people wanted to reserve. We already had the [system] on campus for them to do that, but we wanted them to only have access if they’d booked that space.
It started out in one small building, and we grew from there.
And so that's kind of the room booking kind of reservation type thing.
After that we had another situation where people wanted to control the hours their building was open because it was changing a lot. They wanted to have access to the access control system just for that one little purpose, but we didn’t want to do that.
We decided to try using a Microsoft Outlet calendar.
We said why don't you try it out and see how it goes. It worked great for them, and we've grown it from there.
In both cases, we started with one specific example and then grew as other needs came.
For our housing situation, we just went all in on that. Over a summer we prepped it and when the big move in came for the fall, we had everything set in place and the students had a different experience.
Utilizing DAX from Detrios, we're able to take our schedules from Ad Astra, Mazevo, Office 365, things like that and that's one module that they have.
They have, those integrations already built.
At Auburn, we're able to go in their web configuration module and turn things on and fill out a few fields and it just works.
That's one of the modules they have that handles the unlocking of doors and the creating access for certain periods of time.
Then their housing module is a separate thing, but all within the same web module where we were able to set up our StarRez integration.
Again, they've done all the integration, and we're just configuring it. We're mapping that if you're in this room of this residence hall in StarRez, you have this access level in our OnGuard access control system.
We do that and then it's set it and forget it. We haven't had any issues with that at all.
They have those two different functions all within the same configuration tool.
It doesn't snow much in the south, but we did have a weather day. They have the ability to ignore the events. There were all these calendar events that were coming up where the doors should be unlocked or people should be granted access, but it was decided that we were closing the school down this day.
Rather than having to go into the different scheduling softwares and get rid of [calendar events] or make adjustments, we just had to log into their system and set it to ignore all that stuff. Then we were able to let the access control system and take over, which is where we made the regular adjustments.
No doubt, there are a lot of people working in various different places on campus that don't have to do things anymore that they used to.
I'm sure if I were to sit down and do an analysis, I could come up with a very high return on investment from a numbers standpoint. But just from an effort, usability, efficiency standpoint, the feel that you get is that you got a huge return on investment.
People are very happy; there are tasks they don't have to do any more that they used to have to do. They can focus more on their real job, instead of doing these other things, because the system automatically does it.
It's also helped on mistakes. You used to have to key something in one system, like your scheduling system or StarRez, and then you would either have to go into another system to apply access or change schedules or you would pass it on to another department for them to do. Certainly, you're going to have mistakes when that happens. There's going to be a typo or miscommunication. When it's all tied in, you're making it more efficient, so people don't have to type it in multiple systems and multiple groups aren't having to deal with it.
If you don't have DAX from Detrios, and you have a scheduling system and an access control system that don't talk, you need it or you need something like it. I don't know of anyone else doing the exact thing. They are experts in the arena, and they work well to have the systems communicate with each other in a proper and professional manner using good security techniques, good coding skills, proper APIs, and they maintain that over time.
When you invest in this, you know that it's going to work on this version, I have all the confidence in the world that five years from now, it will continue to work.
If you have a homegrown system, and you think ‘I'm good, it works for me,’ you're going to have to maintain it, and things that are going to change.
That gives me peace of mind, and then, quite honestly, they're really great to work with as well.
It's easy to submit a ticket, and if there is an issue, they will resolve it.
We have a relationship with the company, and that's very important to me. Particularly when we're doing housing stuff, if that's not working and people are trying to move in and they can't get access, that's a big deal.
Knowing that I can pick up the phone and call them or put in a support ticket and get that response is very comforting.
For higher education institutions, managing access to thousands of doors across campuses has always been a daunting task. Universities often have 1,000, 5,000, 10,000 or more access control readers. For full visibility into the environment, each access point requires detailed tracking of location, hardware, firmware versions, and maintenance needs.
ASSA ABLOY’s Openings Studio is designed to streamline this process, enabling universities to manage their access control systems more efficiently and plan for the future.
To better understand how Openings Studio works and the benefits it can deliver for campus card and security operations, CampusIDNews spoke with Ryan McLachlan, Senior Director of Openings Studio Building Technologies at ASSA ABLOY, and Jeff Rindlisbacher, Director of the same division.
When managing their physical access systems, universities face a complex web of data points. Every component requires careful documentation, from wireless locks and readers to physical door components like strikes and frames. But for most organizations, this documentation is fragmented at best.
If there’s an issue at a door – say a card isn’t working – you already have detailed information before sending someone out. That way, you’re not wasting time on a separate trip just to assess the situation.
According to McLachlan there is enormous value in creating a centralized database to track these assets.
While Openings Studio is ideal for managing data for door access points, it was not designed to support other security infrastructure such as cameras, intrusion, panic or duress systems. Another solution called SiteOwl, however, is designed to capture all this additional component data. ASSA ABLOY acquired SiteOwl to complement its Openings Studio solution. Learn more about SiteOwl here.
“Being able to document all of your existing security devices is critical,” he says. “Openings Studio has always been strong on door-centric applications, giving you the ability to collect and manage opening data at a detailed level.”
It goes beyond simple documentation by providing actionable data. Campuses can leverage the platform to align future projects with existing infrastructure, ensuring they make informed decisions about replacements and enhancements.
“It’s all about understanding what’s in the field and where it’s at from a lifecycle perspective,” he explains. “It lets you intelligently plan for upgrades or for bringing new buildings online.”
Openings Studio is a web-based platform with mobile capabilities, making it accessible to teams both on-site and in the field. Field staff can use tablets or smartphones to gather data during site visits, conduct inspections, or troubleshoot issues in real time.
This functionality is beneficial when responding to maintenance calls. Before dispatching a technician, the system provides a complete record of the affected door, ensuring the right tools and parts are brought to the job.
NFC chips or QR codes are attached to doors during installation, upgrades, or as a part of the cataloging process. Scanning these tags reveals key information like the building location, hardware set, and access credentials.
“If there’s an issue at a door – say a card isn’t working – you already have detailed information before sending someone out,” McLachlan explains. “That way, you’re not wasting time on a separate trip just to assess the situation.”
The platform integrates smart tags, such as NFC chips or QR codes, that are attached to doors during installation, upgrades, or as a part of the cataloging process. Scanning these tags reveals key information like the building location, hardware set, and access credentials. Users with higher permissions can even view detailed work history, specifications, and even installation or programming instructions directly from the mobile app.
According to Rindlisbacher, this feature reduces confusion and accelerates problem resolution.
“All the collateral is there at your fingertips,” he says. “It’s about having everything you need in one place, whether you’re maintaining existing doors or working on new construction.”
For campuses migrating to mobile access, Openings Studio provides a perfect opportunity to capture and organize data during the process.
“Large-scale initiatives like a mobile credential rollout are the ideal time to begin collecting detailed door data,” McLachlan explains. “Since you’re already visiting every reader, it makes perfect sense to capture that information in the most organized way possible.”
Universities can create custom inspection templates within the software to track pilot programs or test specific hardware. For example, a school might add fields to confirm whether a door successfully reads the new mobile credentials. This data is easily reportable and can help administrators identify problem areas before a full-scale launch.
Large-scale initiatives like a mobile credential rollout are the ideal time to begin collecting detailed door data. Since you’re already visiting every reader, it makes perfect sense to capture that information in the most organized way possible.”
Even when teams are on-site for a specific project, they can take more time and gather additional valuable data.
“It might start with a rekeying initiative, but while we’re there, we can capture information about fire-rated openings, card readers, and more,” Rindlisbacher says. “That extra data benefits other departments down the road.”
The platform also simplifies project tracking for construction and renovation efforts. The project team can monitor whether hardware has been delivered, installed, and quality-checked before final turnover. By providing transparency across stakeholders – from architects to general contractors to university security teams – Openings Studio can ease the workflow from start to finish.

Universities can use Openings Studio independently or have ASSA ABLOY’s consulting team test credentials and document the components and status of every door and reader
The platform’s non-proprietary database supports hardware from multiple manufacturers, making it flexible for campuses with diverse systems. It also integrates with popular building design solutions, ensuring seamless collaboration between architects, contractors, and campus security teams.
While universities can use Openings Studio independently, many choose to bring in ASSA ABLOY’s consulting teams for large-scale projects. These specialists conduct conditional assessments, test credentials, and document the components and status of every physical opening and access device. For campuses with limited staff, outsourcing this work ensures accuracy and reduces the burden on internal teams.
McLachlan emphasizes that successful implementations require thinking beyond immediate needs.
“There’s often one initiative driving the project, but we always look for additional valuable data points while we’re in the field,” he said. “It’s about planning ahead and understanding the full lifecycle of your security systems.”
Managing thousands of doors and access control devices is challenging for any university, but Openings Studio offers a comprehensive, scalable solution to facilitate the process. By centralizing data, streamlining maintenance, and supporting future initiatives like mobile credential migrations, the platform empowers campus card and security teams to work smarter and more efficiently.
“Ultimately, it’s about providing transparency and future-proofing your operations,” McLachlan concludes. “When you have the right data at your fingertips, you can make better decisions and ensure your campus is ready for whatever comes next.”
Washington State University (WSU) has transformed how students regain access to their residence halls when they’ve lost their campus card. A network of self-service kiosks designed to issue temporary cards provides a way to solve late-night access problems and ease the associated burden on staff.
“Our temporary campus card system started originally as a 24/7 self-service system for students to help them get into their res halls when we're not staffing them 24/7 with RAs,” explains Aly Heinrich, Manager of WSU’s CougarCard program. “Before the kiosks, campus staff were fielding calls at all hours from students who had lost their cards or were locked out with no RA available to help.”
By providing 24/7 access, WSU significantly reduces the need for RA staffing hours, eliminating an estimated 33,000 hours and the associate payroll.
Currently, there are kiosks in seven of the university’s 14 residence halls, with plans to expand to every hall. This will eliminate the challenge of students having to access another residence hall to get a temporary card to use in their own hall.
The kiosks issue simple, low-cost prox cards.
Students log in with their campus credentials, and the system deactivates their regular card while the temporary card is active. Each temporary card is valid for three days and comes with a $20 charge – the same amount as the normal replacement card fee. If the card is returned within two weeks, the fee is automatically refunded.
When finished, students return the card to the kiosk, which immediately makes it available for another user. WSU has about 2,000 cards in circulation, constantly being checked out and recycled.
“It gets used constantly. I checked our temp card data, and a hundred cards have been taken out since I left four days ago.”
“Just today, I checked our temp card data, and a hundred cards have been taken out since I left four days ago,” she says. “It gets used constantly.”
The benefits go beyond student convenience. By providing 24/7 access, WSU significantly reduces the need for RA staffing hours. Heinrich estimates this saves an estimated 33,600 hours of work per year, which even at minimum wage is a significant sum.
Looking ahead, she sees continued value for the system, even as mobile credentials gain popularity. As she explains, there’s still going to be times when students don’t have their phone handy and this can give them a quick, easy way to get back into their room.
To listen to the full interview, click the image at the top of this page.
TRANSCRIPT
Our temporary campus card system started originally as a 24-7 self-service system for students to help them get into their res halls when we're not staffing them 24-7 with RAs.
The problem that it was solving was our office was getting calls in the middle of the night asking, hey, my card's not working, I can't get in my dorm room, what am I supposed to do? There's no RA here.
So we installed temporary card kiosks in seven of our 14 res halls and now students have a 24-7 solution to get into their dorms.
We currently have seven kiosks in seven of our 14 res halls, but we are working on installing a kiosk in every single residence hall on campus.
We run into some students not being able to get into a different residence hall to get into a kiosk, so we're going to eliminate that problem and help them get into their res halls whenever they need.
Currently we are producing only prox cards in the temporary card kiosks.
It's cheap. It's simple.
There's not a huge security concern because they already have to log in with their own campus credentials to get a temporary card.
That temporary card only lasts for three days. It will deactivate their entire campus card account. That way they either have to come get a new campus card or they have to get a new temporary card.
When they're done with the card, the kiosks have an acceptor so they can just log into the kiosk and return their card, and they can actually reactivate their current card as well.
When a student checks out a temporary card, it puts a $20 charge on their account. Our card replacement fee is $20, but if they return that card within a two week period, the refund is automatically applied.
We use Meridian kiosks. They are mostly a hospitality food service kiosk industry, but they've produced a really fantastic piece of hardware for us.
Originally when we were using these kiosks also as card replacement systems, inside of the kiosks we had a card printer, we had a full desktop computer and everything.
Now our kiosk just has the card acceptor, the card dispenser, and the computer in there to manage the computer software system.
Just today actually, I checked our temp card data while I had a break and a hundred extra cards have been taken out since I left four days ago, so it gets used constantly.
We have about 2,000 temporary cards in production that are in recycling mode, so as soon as a student returns a temporary card to a kiosk, it's automatically removed from their account and another student can go and take that and apply it to their account instead.
Our feedback has been awesome.
We thought this might be a cool thing 15 years ago and my team has seen students asking for it more.
Even this year with a student over winter break not being able to get a temporary card because she didn't live in a hall with a kiosk – we heard that and we're going to put a kiosk in every hall now.
It started mostly as student service, but it also really helps our housing department not have to pay their RAs 12 hours a day.
Imagine 14 residence halls, one RA 12 hours a day, that's 14 times 12, times your minimum wage, we saved 33,600 hours of RA work in one year.
So multiply that by your minimum wage and that's how much money we saved.
I was presenting this project to NACCU at this conference and I let the audience know that honestly with all this talk of mobile credential, I get a little nervous that this temporary card system might die off.
It might not be needed if everybody has their phone, but they actually reassured me.
They were like, how many times do you leave your phone in your car when you're packing in your groceries. You get up to your door with your arms full of groceries and you don't have your phone, they would have to drop all their groceries, go all the way back to their car and find their phone.
Now there's a kiosk right down the hall so they can just put their groceries down for a second, go get a card, get in their room, put away the groceries and go get their phone.
As much as I was concerned about it at the beginning of this week, the folks here have really helped me feel a lot better about it, and they showed a lot of interest as well.
So it's been really cool to see the value that this provides for our students and that there is a future with it as well.
It was 20 years ago when Hurricane Katrina hit the Gulf Coast, devastating cities and towns across Louisiana and Mississippi. Nearly 1400 people lost their lives and – adjusted for inflation – it remains the most costly hurricane in U.S. history.
For countless families and individuals, life was changed forever, and negative impacts are still close at hand. But occasionally instances of good come out of even the worst events.
Such was the case when a student ID card that was lost during the storm was returned to its owner at Katrina’s twentieth anniversary.
Driven to solve the mystery, Copeland posted a photo on the high school’s alumni page. It did not take long for people to respond.
While walking a stretch of beach at Gulf Islands National Seashore, park ranger Becky Copeland spotted something in the sand. She unearthed a small piece of history — a beaten but intact student ID card buried below the surface.
"It was so dark and weathered, but still intact," Copeland says during an interview with CBC Radio's As It Happens.
At first, the card seemed like just another item for her collection of unusual finds such as messages in bottles. The only visible clues were the year 1969 and the name of a high school in Birmingham, Alabama.
Unfortunately, the name of the cardholder was no longer visible so Copeland assumed its owner would forever remain a mystery. But recently, while rearranging her collection, she was stunned to see the faded lettering had become legible.
The card belonged to Cathy Hamel, who graduated in 1973.
Driven to solve the mystery, Copeland posted a photo on the high school’s alumni page. It did not take long for people who knew Hamel to respond.
From Katrina’s fury to a heartfelt reunion
Hamel had moved to a small town on the Mississippi coast years before Hurricane Katrina washed away the entire community. The night before the storm, she evacuated to house further inland, but even there the storm surge reached her in the attic. Thankfully, she made it through.
When she returned the following day, her home was completely gone — reduced to a concrete slab and a porch swing hanging from a tree. The few belongings she saved were two photo albums and some insurance papers.
But two decades later, her student ID card that had been lost to the storm resurfaced.
The beachcombing park ranger, Copeland met Hamel at the Gulf Islands National Seashore visitor center, and they embraced immediately.
Hamel called Copeland an angel, “because she did all the legwork to find me to return it."
For Hamel, the recovered ID is far more than a plastic card – it’s a tangible reminder of resilience, loss, and the kindness of strangers.
In this episode of CampusIDNews Chats, Tony Erskine, Founder and CTO of CloudCard, shares how the company’s Remote Photo solution simplifies the process of student ID photo submission. Since its start in 2015, the company has grown into a widely adopted mainstay across higher education, working with all major one card providers.
We’re making it feel like magical photo elves took a picture of your student for you and then dropped it into your one card system.
“Basically, we’re trying to make it feel like magical photo elves went and took a picture of your student for you and then dropped it into your one card system,” says Erskine.
Remote Photo eliminates the need for students to visit the card office, instead allowing them to upload pictures through a streamlined, AI-enhanced workflow. The system automatically removes backgrounds, enforces consistent sizing, and prompts students to resubmit photos if they don’t meet requirements.
When CloudCard first launched, every student photo had to be moderated manually. But as AI technology evolved, the company integrated automated classifiers to approve or reject submissions. Today, a photo goes through about two-dozen classifiers or checks prior to approval.
Some institutions rely fully on automation, while others keep human review in place.
“The students don’t always read, and that’s okay because I don’t always read,” Erskine jokes, highlighting how the system helps students correct mistakes without slowing down the process.
Beyond photos, Remote Photo now supports government-issued ID verification. Students can upload a passport or driver’s license alongside their ID photo, and CloudCard’s system uses facial recognition and optical character recognition (OCR) to confirm identity details. This reduces the burden on card office staff and eliminates the need for in-person verification.
By blending automation with flexibility, Remote Photo not only saves staff time but also meets students where they are—online, mobile, and expecting convenience.
To watch the full interview, click on the image at the top of this page.
I'm Tony from Remote Photo by Cloudcard and we are an online photo submission system that got its start out of Liberty University where I built their system in 2014.
In 2015 we launched right here in NACCU, so it's actually our 10 year anniversary coming to NACU and kind of like a homecoming.
So what do we do?
We capture photos, we make it so that the students don't have to come into the card office at all, especially when you compare it with mobile credentials or something like that.
We provide an AI-enabled workflow because to be honest students always don't always take the best photos, right? So, we'll remove background, we'll crop it, consistent aspect ratio and size and all of that.
And then on top of that we tell them when they do things wrong. Because you know what? The students don't always read and that's okay because I don't always read.
We don't hold them to that. We just tell them we can't take that photo and then we make them take another one.
Basically we're trying to make it feel like magical photo elves went and took a picture of your student for you and then dropped it into your one card system.
We started pretty small back in 2015 with three customers. So, a quick shout out to Pacific, ODU and Mercer University who took a chance on us early on which is super awesome.
And now we are, gosh we've partnered with pretty much all the one card systems. It doesn't really matter who you're working with or what you're doing.
We're kind of the standard for online photo submission in higher ed and it's really great to be here at NACCU and working with all our great partners.
Early on when we built the first iteration of the system, every single photo had to be moderated by a human being, and as we got into the 20-teens computer vision was coming along. In 2017 we built as far as I know the first ID photo classifier where we were able to look at a photo and say yeah this photo belongs on an ID card or no it doesn't.
That has allowed many of our institutions to completely delegate that to what we call “Helper Robot” because you know he's kind of helpful. We've added on to that over the years so we've gone from a single classifier to right now there's there are probably two dozen smart filters that a photo passes through on its way through the workflow.
Some of them will auto deny some of them will auto approve but some of our customers still look at every photo because that's what works for their workflow and that's totally cool.
Speaking of AI, we are now able to take a government issued ID like a passport or driver's license, and we can accept that at the same time we accept their ID photo. Then we do facial recognition, and we do optical character recognition to read the driver's license. We compare their name or their address or whatever it is that you want us to check for on the ID.
Again it allows you to offload some of the work that was previously done by a human where now they don't even need to come in for you to verify their ID. It's really helped out a lot.
If you're interested in learning more about Remote Photo or if it seems like it might be a fit for your organization, you can check us out online. The first step would be for us to schedule a quick 15-minute call to see if there's a fit and if there are problems that we can help you solve. We'd love to talk with you.
In the second article in our series titled Chips, formats, and encryption – we explore card formats. In the previous article, we learned that chips store and process data, but it is the format that defines the specifics of the data – the number of digits in the string and what each area of the string means.
Consider this series of digits, 2024567041. Now look at it this way, (202) 456-7041. An established format defines that a phone number will include ten digits with the first three standardized as the area code.
The format provides order, but the format is not the actual number. That unique number identifies – or dials – the White House.
Similarly, a format defines the way data is stored on the credential, but each cardholder has a unique number.
You often hear an end user say ‘I have a 35-bit card,’ but they are confusing the 35-bit format with the card or chip itself.
For identity and access control professionals, the differences between chips, cards, formats, and numbers are subtle. They are, however, crucial to managing systems.
Understanding the options within each category can ensure you make the most appropriate selections for your campus. It is also crucial in ongoing purchasing processes to make sure you are specifying cards, formats, and numbers that will work in your environment.
Each concept is applicable to both cards and mobile credentials, and understanding them is key to making informed decisions for your campus card program.
“It is always a challenge to explain to customers the difference,” says Todd Brooks, Vice President of Products and Technology at ColorID. “You hear ‘I have a 35-bit card,’ but they are confusing the 35-bit format with the card or chip itself.”
He explains that the same format can be used on any card type, because the format is just the way the data is parsed.
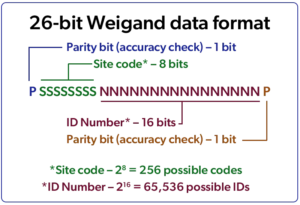
The 26-bit format – also known as the Weigand format – is the oldest and most common. It allows for the smallest number of digits, however, and this provides limitations.
A bit is a binary term for a zero or a one. Thus, 26-bit format consists of 26 zeros or ones laid out in a specific pattern. The initial bits form the three-digit site code with 256 total options. The remaining bits form the ID number with 65,536 options.
The initial bits form the three-digit site code with 256 total options. With that limited number of unique codes for organizations worldwide, there are plenty of duplicates.
The limitation is that with only 256 site codes for organizations around the world, there are plenty of duplicates. While 65,536 seems like a lot of unique numbers, many organizations have thousands of cardholders.
Any card reseller worldwide can issue 26-bit cards so there is no control over numbering systems.
“Because 26-bit is an open protocol, no entity is managing the number range so if care is not taken when placing orders, programmed ID numbers can overlap from one order to the next,” says David Stallsmith, ColorID’s Director of Product Management. “If this occurs, the new batch of cards cannot be entered into your system because the numbers are already in use.”
 Moving beyond 26-bit
Moving beyond 26-bitDespite the industry’s concerns, the 26-bit ‘OG’ format remains difficult to displace.
“It works in everybody's system, and some older access control systems can only handle 26-bit,” says Stallsmith. “Even when systems support longer formats, many security managers are reluctant to use them.”
But he stresses that upgrading to more versatile formats makes sense. That is why security-conscious organizations have moved beyond 26-bit.
We highly recommend against starting with a 26-bit format. HID and Allegion offer formats of 35-bit, 40-bit, 48-bit, and they will manage the number range for you.
“We highly recommend against starting with a 26-bit format,” Stallsmith says. “HID and Allegion offer formats of 35-bit, 40-bit, 48-bit, and they will manage the number range for each customer which is a nice feature.”
The longer the bit structure, the more digits can be stored. The more digits, the more uniqueness for site codes and credential numbers. This is crucial to the successful operation of all the systems that use cards to authenticate and grant access, but it is not the same as data security.
“True security is in the chip and encryption, not in the format,” says ColorID’s Brooks.
There are thousands of other formats, but many are custom and can only be purchased from specific dealers. In some cases, manufacturers will create one for a specific dealer, and they will only supply cards with the format to that dealer.
Dealers often claim that it provides an added layer of security, allowing them to further tighten the grip against card number duplication.
Stallsmith says that this added layer does little to nothing for security, and it forces the end customer to buy all cards through the dealer.
“The real security here is protecting the dealer's business,” jokes Stallsmith. “Make sure you're buying a format that's generally available from all dealers who sell that product.”
Since most campus cards are used in access control systems, they typically use one of the formats described above. In addition to the unique ID number required for the security system, however, the same card will often need to contain one or more additional unique IDs.
A common ID number that is used by the institution’s campus card system provider is a 16-digit ISO number. Additionally, dedicated user IDs for applications like library checkout are sometimes used.
If you are planning to move to mobile, find out from your intended provider what formats they support and consider migrating your card population to that format.
“In some cases, the access and campus card systems themselves are modified to support a single ID that is stored on the card using a single format,” explains Brooks. “But in other cases, the card contains multiple numbers, each designed to support specific functions.”
Modern, multi-application contactless cards are built to support this exact situation. Multiple numbers can be stored in the same contactless card, and each can use a different format.
Though it is not always the case, most modern access control systems can support multiple formats.
But, as Stallsmith explains, end users typically prefer all their credential types to be programmed with the same format.
“If you are planning to move to mobile, find out from your intended provider what formats they support for issuing mobile credentials,” he says. “And consider migrating your card population to that format.”
Three main components underlie modern credential technology – chips, formats, and encryption. Each are applicable to both cards and mobile credentials and understanding them is key to making informed decisions for your campus card program.
Each concept is applicable to both cards and mobile credentials, and understanding them is key to making informed decisions for your campus card program.
In this series of articles, we will dive into each component, but first a brief preview.
Chips are the core of the credential equation. Like the chips that power almost everything we use in our modern lives, they both store and process the data required for identity transactions.
A format – also known as a card format or data format – is the standardized pattern used to store data on a chip. The format holds information such as ID numbers that allow access control and other systems to make decisions about the cardholder. Because data formats are just patterns or structures, they can be used on different chips. This enables different chip types to be used in the same system.
Encryption is the primary method used to secure data on the chip and in transit between the chip, reader, and system. Encryption levels in credentials vary greatly, from none-at-all to best-in-class, and everywhere in between.
In this first of these three articles, we’ll dive into chips.
Most chips on ID cards are either proximity chips that operate at the 125 kHz frequency or contactless smart chips that operate at the higher 13.56 MHz frequency.
The chips used in proximity or prox cards are older, non-secure technology. They do not support encryption and are really a storage mechanism to hold data such as an ID number. Because they lack security, they are extremely easy to clone and thus have fallen out of favor for secure applications like campus credentials.
You can go to a kiosk at Bed Bath & Beyond, insert your prox card or key fob, and they'll give you a duplicate of it.
According to Todd Brooks, Vice President of Products and Technology at ColorID, prox card cloning is easy and inexpensive due to the lack of encryption. There are vending machines and online devices that facilitate cloning.
“You can go to a kiosk at Bed Bath & Beyond, insert your prox card or key fob, and they'll give you a duplicate of it,” says Brooks. “Or you can buy a $25 device on Amazon that can clone cards very easily.”
For these reasons, higher education and most other security-conscious organizations have moved on to high-frequency 13.56 MHz contactless or Near Field Communication (NFC) technology.
But just because these chips operate at a higher frequency doesn't make them inherently more secure. It's what you do with it.
“A lot of people think, oh, it's contactless or NFC, so it's secure,” says David Stallsmith, Director of Product Management for ColorID. “But NFC only defines the communication frequency and a couple other very simple parameters. If it's not encrypted, it's still not much better than prox.”
In practice, however, most implementations of contactless chips do incorporate encryption. Of course, some do it better than others.
Common 13.56 MHz chips include MIFARE Classic and MIFARE DESFire from NXP, iCLASS from HID, and FeliCa from Sony.
Encryption for MIFARE Classic was compromised years ago, so that chip is not used often in secure applications, though it is still common in low-security situations.
For campus cards in the U.S., FeliCa and the initial versions of iCLASS were popular options, but they are not used much for new implementations. Many institutions that deployed them in the past, however, continue to use them.
There have been four versions of DESFire since its introduction in 2002. Today’s gold standard for security is EV3.
iCLASS Seos – the latest version of HID’s iCLASS – is extremely secure, and its usage is rising rapidly, says Stallsmith. While in this case Seos is the name of a specific chip, it can also be a secure identity object that can be used on other chips.
In recent years, DESFire has been the go-to for campuses and other markets seeking a secure credential.
There have been four versions of DESFire since its introduction in 2002. DESFire, DESFire EV1, DESFire EV2, and DESFire EV3.
According to Brooks, today’s gold standard for security is EV3.
The original DESFire product was phased out by NXP years ago, and EV2 was phased out more recently as NXP released the successor EV3 chip.
Because of its widespread use, EV1 is still available, though its phase out is also starting.
“EV1 still uses high-end AES encryption,” says Brooks. “It hasn't been broken, but we're just seeing NXP starting to phase it out.”
That leaves EV3 as the clear leader for new implementations.
“Many of our campus clients opt for EV3, and that is what we’ve been recommending for some time now,” says Stallsmith. “Because it was designed for backwards compatibility, it can even be blended into existing implementations that utilize prior DESFire versions.”
The other key component with chips is memory size. The larger the non-volatile memory, the more data and applications the chip can hold. DESFire EV3 chips are available in 2k, 4k, 8k, an 16k sizes.
iCLASS Seos chips are available in 8K and 16K.
Often you will hear the terms like 26-bit and 32-bit discussed when talking about contactless cards, but don’t confuse this with a chip’s memory size. These terms refer to data formats, the topic for the next article in this series.
Obviously, older less secure technology is going to be less expensive, but there are also large variances in the quality of a card’s manufacture.
It follows then that low-quality prox and MIFARE Classic cards are typically the least expensive, often just a couple bucks. But high-quality cards with the same chip can be significantly more expensive.
With any card, however, when it comes to longevity, durability, and good-looking printing, you get what you pay for.
Because of their low cost, many organizations still use non-secure prox and MIFARE Classic cards. Some are not aware of the security vulnerabilities and others choose to take the risk. If the use cases for the card are not high risk in nature, it can be a sensible decision.
With any card, however, when it comes to longevity, durability, and good-looking printing, Brooks says you get what you pay for.
“You can find inexpensive high-frequency cards, but you can also get cards – depending on what you've done with them – that are $10,” he adds. “So, there's a huge range in what you can get from high frequency.”
Here’s what campus card and security personnel should remember about chips for ID cards.
Palm Beach State College’s campus card office has opted to forego mobile credentials and stick with their longtime magstripe cards. While the decision may seem unusual to some, Jessica Bender, the college’s auxiliary services manager, explains to CampusIDNews the rationale and the research that went into it.
With a student population of 40,000, the college would face significant costs in transitioning to mobile, including annual licensing fees of $2 to $5 per credential. This compares to a onetime cost of just 25 cents per magstripe card.
She emphasizes that as a commuter-based community college, students don’t use their ID cards daily.
I don't think our students suffer by us not going mobile. As a community college, I'm not sure that they even know about it.
Most ID usage is tied to periodic events such as printing, financial aid transactions at the bookstore, or accessing the wellness center. They don’t have door access or meal plans that typically justify mobile adoption.
The average student age is between 23 and 26, and most live in the surrounding community.
If the college expands door access requirements to all students, the cost-benefit equation could shift. Then, Bender says, they would be open to reconsidering the decision.
She stresses that implementing mobile credentials should not be driven by trends. Incorporate careful evaluation of infrastructure, budget models, and long-term costs – including lost revenue from card replacements.
To watch the full interview, click the image at the top of this page.
Transcript
Our college has decided right now not to go mobile. One of the reasons is we're a very large community college and our use case doesn't really lend itself to mobile.
We have about 40,000 students, and we're still using magstripe cards. The cost is 25 cents a card.
To move to the mobile is a huge cost. We're carding 40,000 students. You have $2 to $5 annual cost per mobile.
We're not doing door access. We're not doing meal plans. We're doing mostly just stored value. So, for now, the magstripe works for us. That's why we decided no mobile for now.
I don't think our students suffer by us not going mobile.
Being a community college, I'm not sure that our students even know about it.
I hear the story that mobile makes the student decide whether they go to college A or college B. It gets a little bit different in the community college market because students stay near home to go to college.
Our students are not 18 to 21-year-olds. They're 23 to 26-year-old average.
I don't think that our students are suffering because we haven't gone mobile.
As a community college, we are all commuters, meaning we don’t have the residence halls so students don't need their card every day.
You know, I hear universities say that's why they found mobile because students always have their phone.
At a community college, the things students need their card for like printing, so you're not doing that every day. Financial aid at the bookstore, that's a semester thing. They want to maybe go to wellness center, so they need their card for that.
But it's not like a residential campus where you constantly need to present the credential.
I think that you really have to look at your use case to see if that makes sense.
That's funny that you should bring up when we might consider mobile. I was just in a meeting last week and we're slowly moving towards door access for our academic buildings. I was told by our chief safety officer that her goal is to have everything locked down 24x7.
And what that would mean would be someone would have to have a credential to present to get into buildings.
Right now we are using a MIFARE card for certain staff to have a limited amount of door access. But if you turned around and told me that from now on, every student was going to need to get that MIFARE card, so now you're at that same kind of price point at $5.
If that's where we get to, then I would say at that point that would change the conversation. Because you can save some costs by eliminating printers, eliminating staff at the printing locations, and still, you're going to be spending $5 on a MIFARE card. So I could spend $2 to $5 on the licensing for the mobile.
I just think when making a decision about mobile, it's a case by case decision and every school is going to be different.
I think some schools went with it because it was the cool, shiny thing to do, but I think you have to think about it.
Coming to things like NACCU and reading up on the industry, can help you understand all the costs involved.
Yes, the shiny new thing, but what I didn't know until I talked to a school that went mobile is it's an ongoing annual cost.
You have to have the infrastructure and the budget model to support that, and then you lose some income.
You lose your replacement fees and things like that, so you really need to make an informed decision and get all the facts before you decide, well, I'm going to do the shiny thing by going mobile.

